Transcription of CISSP Prep: 4 Steps to Achieve Your Certification
1 E-guide CISSP Prep: 4 Steps to Achieve your Certification Practice for the exam and keep your skills sharp Page 1 of 11 In this e-guide step 1: Test step 2: Study step 3: Practice step 4: Schedule About SearchSecurity E-guide In this e-guide: Thank you for downloading our CISSP Certification guide. Aside from this handy PDF, you can also access critical CISSP Certification information on Obtaining CISSP Certification is globally recognized as a standard of achievement for security professionals.
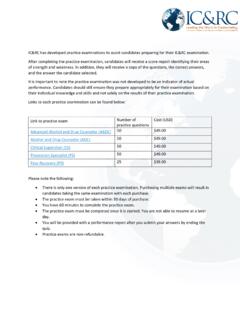
2 Today, many large corporations and governmental agencies now require the Certification for a position, thus giving CISSPs a higher earning potential and greatly expanded career opportunities. In partnership with global information security educator and Certification leader (ISC) , is providing information security professionals tools and resources to earn and maintain your CISSP Certification . Page 2 of 11 In this e-guide step 1: Test step 2: Study step 3: Practice step 4: Schedule About SearchSecurity E-guide step 1: Test your Knowledge First, test your knowledge by taking the CISSP practice exam.
3 This is a free benefit to members. We encourage you to come back often while you are studying for the CISSP . Page 3 of 11 In this e-guide step 1: Test step 2: Study step 3: Practice step 4: Schedule About SearchSecurity E-guide step 2: Study for the CISSP Test with Trainings a n d Te x t s Learn more about CISSP domains The CISSP exam covers 8 subject areas, which are referred to as domains. These domains are drawn from various security topics within the (ISC) Common Body of Knowledge, a framework of best practices , methodologies, technologies, and concepts.
4 The CISSP candidate must have at least 5 years of paid full-time experience in 2 or more of the domains. Prepare for the 8 domains listed below with 10 free lessons from SearchSecurity s CISSP Essentials Security School, featuring videos, tutorials, and sample exam questions. Page 4 of 11 In this e-guide step 1: Test step 2: Study step 3: Practice step 4: Schedule About SearchSecurity E-guide The 10 lessons in CISSP Essentials Security School are broken down into three domain groups.
5 The first three domains focus on securing assets and reveal the essential elements to build an organizational enterprise security program, including the frameworks, technologies and methodologies to protect every company's primary information asset: its data. Domains 4-6 focus on securing the infrastructure as they reveal the nuts and bolts of how to best apply security to everyday computer and business operations. Fundamental concepts explored in the sessions include how to effectively design security architectures, implement secure networks and build security into applications and systems.
6 Finally domains 7-10 cover the business of security, an area that is ignored far too often in some of today's "status quo" enterprises. Security is often thought of exclusively in terms of technology, but corporate security is much more. It involves everything from governance, business management and regulatory compliance, to an understanding of physical security, disaster recovery and the law. Page 5 of 11 In this e-guide step 1: Test step 2: Study step 3: Practice step 4: Schedule About SearchSecurity E-guide An Overview of the 8 CISSP Domains Security and Risk Management (Security, Risk, Compliance, Law, Regulations, and Business Continuity) Confidentiality, integrity, and availability concepts Security governance principles Compliance Legal and regulatory issues Professional ethic Security policies, standards, procedures and guidelines Asset Security (Protecting Security of Assets) Information and asset classification Ownership ( data owners, system owners)
7 Protect privacy Appropriate retention Data security controls Handling requirements ( markings, labels, storage) Security Engineering (Engineering and Management of Security) Engineering processes using secure design principles Security models fundamental concepts Security evaluation models Page 6 of 11 In this e-guide step 1: Test step 2: Study step 3: Practice step 4: Schedule About SearchSecurity E-guide Security capabilities of information systems Security architectures, designs, and solution elements vulnerabilities Web-based systems vulnerabilities Mobile systems vulnerabilities Embedded devices and cyber-physical systems vulnerabilities Cryptography Site and facility design secure principles Physical security Communication and network Security (Designing and Protecting network Security) Secure network architecture design ( IP & non-IP protocols, segmentation)
8 Secure network components Secure communication channels network attacks Identity and Access Management (Controlling Access and Managing Identity) Physical and logical assets control Identification and authentication of people and devices Identity as a service ( cloud identity) Third-party identity services ( on-premise) Access control attacks Page 7 of 11 In this e-guide step 1: Test step 2: Study step 3: Practice step 4: Schedule About SearchSecurity E-guide Identity and access provisioning lifecycle ( provisioning review) Security Assessment and Testing (Designing, Performing, and Analyzing Security Testing) Assessment and test strategies Security process data ( management and operational controls) Security control testing Test outputs ( automated, manual) Security architectures vulnerabilities Security Operations (Foundational Concepts, Investigations, Incident Management, and Disaster Recovery)
9 Investigations support and requirements Logging and monitoring activities Provisioning of resources Foundational security operations concepts Resource protection techniques Incident management Preventative measures Patch and vulnerability management Change management processes Recovery strategies Disaster recovery processes and plans Page 8 of 11 In this e-guide step 1: Test step 2: Study step 3: Practice step 4: Schedule About SearchSecurity E-guide Business continuity planning and exercises Physical security Personnel safety concerns Software Development Security (Understanding, Applying, and Enforcing Software Security) Security in the software development lifecycle Development environment security controls Software security effectiveness Acquired software security impact Buy the Official (ISC) Guide to the CISSP CBK Find all official ISC textbooks here.
10 All (ISC) members receive 50% off Official (ISC) Textbooks as a member benefit. Page 9 of 11 In this e-guide step 1: Test step 2: Study step 3: Practice step 4: Schedule About SearchSecurity E-guide step 3: Retake the CISSP Practice Exam This practice session will offer you a preview of 20 questions pulled straight from previous CISSP exams to give you a sneak peak of what the Certification exam entails. Come back daily for a new batch of questions and check out our related study resources to help boost your score.