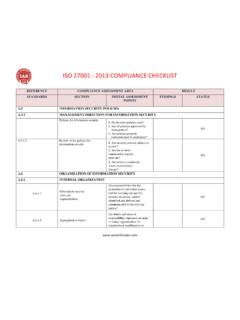
Transcription of ISO 27001-2013 Auditor Checklist - RapidFireTools
1 ISO 27001 - 2013 Auditor Checklist01/02/2018 The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001 : 2013 . The Checklist details specific compliance items, their status, and helpful references. Use the Checklist to quickly identify potential issues to be re-mediated in order to achieve ComplianceReferencesIssues5 Information security direction for information for information securityYesYesInformation Security Policies and of the policies for information securityYesYesInformation Security Policies and Procedures - Review; ISO 27001 Compliance Questionnaire - Information Security Policy; Evidence of Compliance - Information Security Policies6 Organization of information security roles and responsibilitiesYesYesInformation Security Policies and Procedures - Security Roles and of dutiesYesYesInformation Security Policies and Procedures - Security Roles and with authoritiesYesNoInformation Security Policies and Procedures - Contact with Authorities; ISO 27001 Compliance Questionnaire - Contact with authorities.
2 Evidence of Compliance - Organisation of Information SecuritySee Risk Treatment with special interest groupsYesNoInformation Security Policies and Procedures - Contact with special interest groups; ISO 27001 Compliance Questionnaire - Contact with special interest groups; Evidence of Compliance - Organisation of Information SecuritySee Risk Treatment security in project managementYesNoInformation Security Policies and Procedures - Information security in project management; ISO 27001 Compliance Questionnaire - Information security in project management; Evidence of Compliance - Organisation of Information SecuritySee Risk Treatment devices and device policyYesYesInformation Security Policies and Procedures - Mobile Device Policy; ISO 27001 Compliance Questionnaire - Mobile Device and Teleworking; Evidence of Compliance - Organisation of Information SecurityISO 27001 - 2013 Auditor Checklist01/02/2018 The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001 : 2013 .
3 The Checklist details specific compliance items, their status, and helpful references. Use the Checklist to quickly identify potential issues to be re-mediated in order to achieve Security Policies and Procedures - Teleworking; ISO 27001 Compliance Questionnaire - Mobile Device and Teleworking; Evidence of Compliance - Organisation of Information resource to Security Policies and Procedures - Human Resource Security; ISO 27001 Compliance Questionnaire - Human Resource and conditions of employmentYesYesInformation Security Policies and Procedures - Human Resource Security; ISO 27001 Compliance Questionnaire - Human Resource responsibilities YesYesInformation Security Policies and Procedures - Human Resource security awareness, education, and trainingYesNoInformation Security Policies and Procedures - Information Security Awareness and Training; ISO 27001 Compliance Questionnaire - Information Security Awareness and TrainingSee Risk Treatment processYesYesInformation Security Policies and Procedures - Human Resource and change of or change of employment responsibilitiesYesYesInformation Security Policies and Procedures - Human Resource for of assetsYesYesAsset Inventory of assetsYesYesAsset Inventory use of assetsYesYesInformation Security Policies and Procedures - Asset of assetsYesYesInformation Security Policies and Procedures - Asset Management; ISO 27001 Compliance Questionnaire - Employee classificationISO 27001 - 2013 Auditor Checklist01/02/2018 The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001 : 2013 .
4 The Checklist details specific compliance items, their status, and helpful references. Use the Checklist to quickly identify potential issues to be re-mediated in order to achieve of informationYesYesInformation Security Policies and Procedures - Information Classification and of informationYesNoInformation Security Policies and Procedures - Information Classification and Labeling; ISO 27001 Compliance Questionnaire - Information Classification and LabelingSee Risk Treatment of assetsYesYesInformation Security Policies and Procedures - Information Classification and of removable mediaYesNoInformation Security Policies and Procedures - Management of removable media; Site Walkthrough ChecklistSee Risk Treatment of mediaYesNoInformation Security Policies and Procedures - Management of removable media; Site Walkthrough ChecklistSee Risk Treatment media transferYesYesInformation Security Policies and Procedures - Management of removable media.
5 ISO 27001 Compliance Questionnaire - Media for control policyYesYesInformation Security Policies and Procedures - Access control policy; Evidence of Compliance - User to networks and network servicesYesYesInformation Security Policies and Procedures - Access control policy; Evidence of Compliance - User for registration and de-registrationYesYesInformation Security Policies and Procedures - Access control policy; Evidence of Compliance - User access provisioningYesYesInformation Security Policies and Procedures - Access control policy; Evidence of Compliance - User of privileged access rightsYesYesInformation Security Policies and Procedures - Access control policy; Evidence of Compliance - User AccessISO 27001 - 2013 Auditor Checklist01/02/2018 The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001 : 2013 . The Checklist details specific compliance items, their status, and helpful references.
6 Use the Checklist to quickly identify potential issues to be re-mediated in order to achieve of secret authentication information of usersYesYesInformation Security Policies and Procedures - Access control policy; Evidence of Compliance - User of user access rightsYesNoInformation Security Policies and Procedures - Access control policy; User Access Rights Review Worksheet; Evidence of Compliance - User Access ManagementSee Risk Treatment or adjustment of access rightsYesYesInformation Security Policies and Procedures - Access control policy; Evidence of Compliance - User of secret authentication informationYesYesInformation Security Policies and Procedures - User and application access access restrictionsYesNoInformation Security Policies and Procedures - Access Control Policy; Evidence of Compliance - User access managementSee Risk Treatment log-on proceduresYesYesInformation Security Policies and Procedures - Access Control Policy; Evidence of Compliance - User access management systemYesNoInformation Security Policies and Procedures - Access Control Policy; Evidence of Compliance - User access managementSee Risk Treatment of privileged utility programsYesNoInformation Security Policies and Procedures - Access Control Policy; Evidence of Compliance - User access managementSee Risk Treatment control to program source codeYesNoInformation Security Policies and Procedures - Access Control Policy; ISO 27001 Compliance Questionnaire - Access control to program source.
7 Evidence of Compliance - User access managementSee Risk Treatment controlsISO 27001 - 2013 Auditor Checklist01/02/2018 The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001 : 2013 . The Checklist details specific compliance items, their status, and helpful references. Use the Checklist to quickly identify potential issues to be re-mediated in order to achieve on the use of cryptographic controlsYesNoInformation Security Policies and Procedures - Cryptography; ISO 27001 Compliance Questionnaire - Cryptography; Evidence of Compliance - CryptographySee Risk Treatment managementYesNoInformation Security Policies and Procedures - Cryptography; ISO 27001 Compliance Questionnaire - Cryptography; Evidence of Compliance - CryptographySee Risk Treatment and environmental security security perimeterYesNoInformation Security Policies and Procedures - Physical and environmental security; Site Walkthrough ChecklistSee Risk Treatment entry controlsYesNoInformation Security Policies and Procedures - Physical and environmental security.
8 Site Walkthrough ChecklistSee Risk Treatment offices, rooms and facilitiesYesNoInformation Security Policies and Procedures - Physical and environmental security; Site Walkthrough ChecklistSee Risk Treatment against external and environmental threatsYesYesInformation Security Policies and Procedures - Physical and environmental in secure areasYesYesInformation Security Policies and Procedures - Physical and environmental and loading areasYesYesInformation Security Policies and Procedures - Physical and environmental siting and protection YesYesInformation Security Policies and Procedures - Physical and environmental security; Site Walkthrough utilitiesYesYesInformation Security Policies and Procedures - Physical and environmental securityYesNoInformation Security Policies and Procedures - Physical and environmental security; Site Walkthrough ChecklistSee Risk Treatment maintenanceYesYesInformation Security Policies and Procedures - Physical and environmental securityISO 27001 - 2013 Auditor Checklist01/02/2018 The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001 : 2013 .
9 The Checklist details specific compliance items, their status, and helpful references. Use the Checklist to quickly identify potential issues to be re-mediated in order to achieve of assetsYesYesInformation Security Policies and Procedures - Physical and environmental of equipment and assets off-premises YesYesInformation Security Policies and Procedures - Physical and environmental disposal or re-use of equipmentYesYesInformation Security Policies and Procedures - Physical and environmental user equipmentYesNoInformation Security Policies and Procedures - Physical and environmental security; Evidence of Compliance - Screen Lock SettingsSee Risk Treatment desk and clear screen policyYesNoInformation Security Policies and Procedures - Physical and environmental security; Evidence of Compliance - Screen Lock Settings; Site Walkthrough ChecklistSee Risk Treatment procedures and operating proceduresYesYesInformation Security Policies and Procedures - Documented operating procedures.
10 ISO 27001 Compliance Questionnaire - Documented operating managementYesYesInformation Security Policies and Procedures - Documented operating managementYesYesInformation Security Policies and Procedures - Documented operating of development, testing and operational environmentsYesYesInformation Security Policies and Procedures - Documented operating procedures; Asset inventory from against malwareYesNoInformation Security Policies and Procedures - Protection from malware; Evidence of Compliance - Endpoint SecuritySee Risk Treatment Backup YesYesInformation Security Policies and Procedures - Backup; Evidence of Compliance - and MonitoringISO 27001 - 2013 Auditor Checklist01/02/2018 The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001 : 2013 . The Checklist details specific compliance items, their status, and helpful references. Use the Checklist to quickly identify potential issues to be re-mediated in order to achieve loggingYesNoInformation Security Policies and Procedures - Logging and monitoring; Evidence of Compliance - Logging and monitoring; Login History ReportsSee Risk Treatment of log informationYesNoInformation Security Policies and Procedures - Logging and monitoring; Evidence of Compliance - Logging and monitoring; Login History ReportsSee Risk Treatment and operator logYesNoInformation Security Policies and Procedures - Logging and monitoring; Evidence of Compliance - Logging and monitoring; Login History ReportsSee Risk Treatment synchronizationYesNoInformation Security Policies and Procedures - Logging and monitoring; Evidence of Compliance - Logging and monitoring.