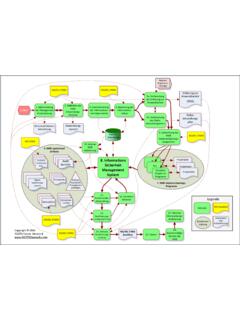
Transcription of Visio-ISO27k preventive action procedure - …
1 PurposeScopeR E V I S I O N H I S T O R YNo Revision DetailsEffectivity Date0 Initial issue2009 06 0312 Revision Stat0 RESPONSIBILITYPROCESS FLOWD ocument TitlePREVENTIVE action PROCEDURED ocument Ref NoI27 KIForum-ROR-PAApproved byPage/Total1/2 Original Author:Richard O. RegaladoAuditorObserverThe purpose of this procedure is to have a defined method in applying preventive actions to eliminate the cause of potential non-conformities on the established information security management system (ISMS).This procedure covers the collection of data on potential non-conformities, analysis of the potential root causes of nonconformities and action planning to prevent occurrence of Non-conformance Corrective action / preventive action report (NCPAR) to concerned person or auditeeDETAILSE stablish preventive action based on root-cause analysisEnter details in the NCPAR Log Lead Auditor shall monitor NCPAR Log on a weekly basis to verify open potential non-conformities and ensure timeliness of follow-up AuditorAuditorObserverAuditorObserverRef er to instructions on page 2 of NCPAR for proper usageApply immediate or containment action to arrest the non-conformityRoot cause analysis tools such as the why-why analysis and Ishikawa diagram shall be used to identify potential root causes of the s managementDetermine potential root cause of the non-conformityAuditeeAuditee s managementPreventive actions shall be applied in a holistic manner with efforts done to ensure applicability on other areas or AuditorAuditorPreventive
2 action is valid?NoYesFor preventive action to be valid, it shall ensure non-occurrence of the follow-up audit within 3 days after the committed date of shall be performed to ensure implementation of preventive Auditor2 This work is copyright 2007,Richard O. Regalado and iso27k implementers' forum, some rights reserved. It is licensed under the Creative Commons Attribution-Noncommercial-Share Alike License. You are welcome to reproduce, circulate, use and create derivative works from this provided that (a) it is not sold or incorporated into a commercial product, (b) it is properly attributed to the iso27k implementers' forum ), and (c) derivative works are shared under the same terms as this.).Identify potential non-conformitiesPotential non-conformities maybe in the form of findings during internal audits (improvement potentials), suspected information security weaknesses and suggestions by [company] the extent or gravity of the potential non-conformityRevision Stat0 RESPONSIBILITYPROCESS FLOWD ocument TitlePREVENTIVE action PROCEDURED ocument Ref NoI27 KIForum-ROR-PAPage/Total2/2 DETAILSP erform 2ndfollow-up 3 months after committed implementation date1 Follow-up shall be performed to ensure implementation of corrective action is implemented?
3 NoYesIssue new NCPAR2 preventive action is effective?YesIssue new NCPAR2 NoClose out non-conformity by making proper notations on the NCPAR AuditorLead AuditorLead AuditorLead AuditorFile and maintain all records in accordance with Control of records procedureLead AuditorThis work is copyright 2007,Richard O. Regalado and iso27k implementers' forum, some rights reserved. It is licensed under the Creative Commons Attribution-Noncommercial-Share Alike License. You are welcome to reproduce, circulate, use and create derivative works from this provided that (a) it is not sold or incorporated into a commercial product, (b) it is properly attributed to the iso27k implementers' forum ), and (c) derivative works are shared under the same terms as this.).As a result of internal auditsInstances where potential non-conformities may be identifiedObserved improvement potentials are possible sources of preventive of information security weaknessesWeaknesses shall be issued appropriate preventive actions lest they become full-blown information security and health and safety near-misses shall be issue corresponding preventive actions before they become accidents.