Emails
Found 9 free book(s)Useful Phrases - cuni.cz
iuuk.mff.cuni.czthat you receive in the emails sent to you by native English speakers. You can then paste these into your own emails. This chapter presents lists of frequently used phrases that have a general acceptance in all types of emails, not just in academia. This means that they are phrases that your recipients will frequently encounter.
How to Auto-Delete Spam Emails in Outlook
www.menlo.eduHow to Auto-Delete Spam Emails in Outlook Introduction Menlo College email is handled by Google Apps for Education. This service provides many benefits, but it also makes it difficult to weed out spam from specific users. Since Google handles our spam filtering, OIT is unable to block specific users whose emails you may not wish to receive.
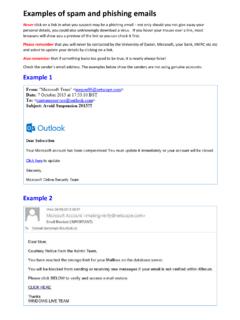
Examples of spam and phishing emails - University of Exeter
as.exeter.ac.ukExamples of spam and phishing emails Never click on a link in what you suspect may be a phishing email – not only should you not give away your personal details, you could also unknowingly download a virus. If you hover your mouse over a link, most browsers will show you a preview of the link so you can check it first.
Corporate Emails - Contexts and Language
repositorio.ipl.ptour own personal collection of useful phrases, which we can cut and paste from emails written, specially by native English speakers. If we make literal translations into English, the result may sound strange or even comical and thus sound unprofessional. This document is divided into categories and subcategories presenting contexts and language
Encryption Guide for NHSmail - Amazon S3
s3-eu-west-1.amazonaws.comIn addition to being able to send encrypted emails using [secure], NHSmail users who use Outlook to access their email accounts can download a free Outlook tool (known as an addin). This enables users to send encrypted emails without using [secure]. Information on how to download the Egress Outlook add-in is available on the NHSmail support site.
What to do if you’ve received a threatening email ...
www.ncsc.gov.ukemails in the hope that someone will pay. They'll often include technical sounding details to make the email sound convincing. It may also include a password the victim uses or has used. d Sextortion is an example of a phi shing attack, where victims receive emails that try and tric k them into doing the wrong
Sample Meeting Agendas and Emails for Mentors
wms.arizona.eduSample Meeting Agendas for Mentors. Suggested Agenda for Meeting #1 The first meeting is crucial to setting expectations and goals for your mentorship.
J.P. Morgan Access RSA SecurID Software Token FAQs
www.jpmorgan.comApr 14, 2020 · A Once your Security Administrator sets you up with a software token, you will receive two emails: • One email will contain the User ID and two documents attached: the J.P. Morgan Access® New User Quick Start Guide and RSA Secure ID® “Registering a Software Token on your device”
WRITING AN INFORMAL E-MAIL or LETTER Read the following …
www.carmenlu.comWRITING AN INFORMAL E-MAIL or LETTER - 3 - www.carmenlu.com 12. We say Best wishes, / Regards, with people we don’t know much. But we say Lots of love, /Love, with close friends and relatives. 13. We sign the text at the end. 14. We write our name at the end.