Search results with tag "Cyber"
CHAPTER II CYBER CRIME AND ITS CLASSIFICATION - …
www.bbau.ac.indark 1sides too. Some of the newly emerged cybercrimes are cyber-stalking, cyber-terrorism, e-mail spoofing, e-mail bombing, cyber pornography, cyber-defamation etc. Some conventional crimes may also come under the category of cybercrimes if they are committed through the medium of computer or Internet. 2.
Toward a Knowledge Graph of Cybersecurity Countermeasures
d3fend.mitre.orgAssessment Language (OVAL ... created the Cyber Threat Framework to serve as a shared lexicon to characterize and categorize cyber threat events [13]. The National Security Agency’s Technical Cyber Threat ... cyber knowledge architecture and provide a useful survey of cyber-related knowledge representations and standards to
EY Cyber Security and Data Privacy
assets.ey.comDec 08, 2020 · Page 4 An overview of our EY Advisory Cybersecurity services Benefits Provide a clear picture of current cyber risk posture and capabilities, giving management and directors a view of how, where and why to invest in managing cyber risks. Implement and execute a strategy and overarching cyber program that allows for rigorous, structured decision making
National Cyber Security Policy - Ministry of Electronics ...
meity.gov.inSubject: Notification on National Cyber Security Policy-2013 (NCSP—2013) National cyber Security Policy- 2013(NCSP-2013) Preamble I. Cyberspacel is a complex environment consisting of interactions between people, software and services, supported by worldwide distribution of information and communication technology (ICT) devices and networks, 2.
A STUDY OF AWARENESS OF CYBER CRIME AMONG …
acadpubl.euCredit/debit card frauds, cyber terrorism and many more crimes. Cybercrimes can occur to anyone if their inform ation or data is stored in the network. Cybercrimes create a nuisance for the law enforcement. This is because these crimes are extremely difficult to trace back to the criminal.
Guideline - Technology and Cyber Risk Management
www.osfi-bsif.gc.caand support business needs and can result in financial loss. “Cyber risk” or “cyber security risk” is the risk of financial loss, operational disruption or ... management and oversight of technology and cyber security. 2. ... Technology Resilience – Sets OSFI’s expectations for capabilities to deliver technology
The Russia-Ukraine Conflict: Cyber and Information …
www.files.ethz.chThe Russia-Ukraine Conflict: Cyber and Information Warfare in a Regional Context What lessons can we learn from Russia’s cyber and information campaigns against Ukraine? According to Tim Maurer and Scott Janz, we should expect them to become more integrated, ... This sudden outbreak of violence.
DIRECTIVE OF THE EUROPEAN PARLIAMENT AND OF THE …
ec.europa.eufemicide, hate speech and crimes on the basis of sex and various forms of online violence (‘cyber violence’), including non-consensual sharing or manipulation of intimate material, cyber stalking and cyber harassment. Such violence is rooted in gender inequality being a manifestation of structural discrimination against women.
The Application of International Law to State Cyberattacks
www.chathamhouse.orgNov 29, 2019 · that over 22 states are responsible for sponsoring cyber operations that target other states, and the number and scale of these operations is growing.1 Cyber operations that cause injury or death to persons or damage or destruction of objects could amount to a use of force or armed attack under the UN Charter
State of Michigan
www.michigan.govOct 25, 2015 · partners, developed the Michigan Cyber Disruption Response Strategy in 2013. To keep pace with the ever-evolving threats, we are proud to present the Michigan Cyber Disruption Response Plan. The Plan provides guidelines to partner organizations to best protect Michigan’s critical cyber infrastructure.
UNITED STATES COAST GUARD CYBER STRATEGIC
www.uscg.milHomeland Security (DHS), the Department of Defense (DOD), our government partners, ... The U.S. Coast Guard will embed cyber planning in our traditional missions and execute cyberspace operations that combine the service’s unique authorities, capabilities, and workforce to deliver mission success. Through our role in DHS and the DOD’s Joint ...
Investigating and Prosecuting Cyber Crime: Forensic ...
www.cybercrimejournal.comthe commission of traditional crimes, including offences against property and offences causing personal harm (McQuade, 2006), existing national legal frameworks may be incapable of addressing evolving ‘modus operandi’ related to cyber crime offending (Hughes, 2003). It is common for cyber crime to be transnational in terms of the physical
Item 2a(iii) CIP-010-3 clean apr 17 2017
www.nerc.comCIP-010-3 – Cyber Security — Configuration Change Management and Vulnerability Assessments . Page 3 of 47 . 4.2.3.2. Cyber Assets associated with communication networks and data communication links between discrete Electronic Security Perimeters. 4.2.3.3. The systems, structures, and components that are regulated by
Regulatory approaches to enhance banks’ cyber-security ...
www.bis.orgCyber-security continues to be assessed largely as part of the ongoing risk-based supervisory framework and, more recently, this has been complemented by thematic reviews. However, supervisors seem to be converging towards undertaking a so-called “threat-informed” or “intelligence-led” testing framework, ie by using threat intelligence ...
WEBELOS BADGE REQUIREMENTS ... - Boy Scouts of America
filestore.scouting.orgRank advancement is awarded when each Scout has done the following: 1. Be an active member of your Webelos den for three months. ... A Parent’s Guide. 5. Earn the Cyber Chip award for your age. (The Cyber Chip portion of this requirement ... With adult guidance, help younger Scouts by leading them in a fitness game or games.
Deloitte’s Cyber Risk capabilities Cyber Strategy, Secure ...
www2.deloitte.comInfrastructure Protection 16 Vulnerability Management 18 Application Protection 20 ... with the findings of a maturity assessment. Recommendations are based on a defined target state that is determined by the ... approach to understanding the road ahead.
Enterprise Security Architecture for Cyber Security
www.opengroup.orgSource: 9 Steps to Cyber Security – The Manager’s Information Security Strategy Manual (Dejan Kosutic) ... Planning. This is followed by an activity called Design, which embraces the design of the logical, physical, component, and service management architectures. The third activity is Implement, followed by Manage & Measure.
Pennsylvania’s New Right to Know Law - PA.Gov
www.jcjc.pa.govFeb 14, 2008 · (1) Any political subdivision, intermediate unit, charter school, cyber charter school or public trade or vocational school. (2) Any local, intergovernmental, regional or municipal agency, authority, council, board, commission or similar governmental entity. “Office of Open Records.” The Office of Open Records established in section 1310.
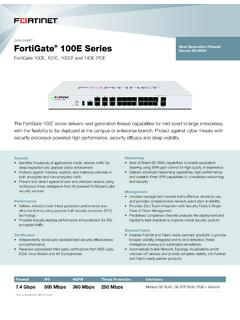
FortiGate 100E Series Data Sheet - Firewalls.com
www.firewalls.comProtect against cyber threats with security processor powered high performance, security efficacy and deep visibility. Security § Identifies thousands of applications inside network traffic for ... Europe, Middle East, and Asia, FortiCare offers services to meet
RESOLUTION MSC.428(98) (adopted on 16 June 2017) …
wwwcdn.imo.orgMaritime Safety Committee, at its ninety-eighth session (7 to 16 June 2017), which provides high-level recommendations for maritime cyber risk management that can be incorporated into existing risk management processes and are complementary to the safety and security management practices established by this Organization,
Unit 8 Project management
www.ocr.org.ukinformation and Unit 3 Cyber security) D2: Create a Business Case to support an identified project P4: Develop a project plan for the identified project M2: Carry out and document a phase review of the project plan 3. Be able to execute projects P5: Follow the project plan and conduct a phase review of the identified project D3:
Employment Equity Act: Code of Good Practice on Prevention ...
www.gov.zaViolence and Harassment against women, men and LGBTQIA + persons in the world of work is an abuse of power. Violence and Harassment particularly affect workers in the most ... CYBER BULLYING refers to the inappropriate use of technology, expression of psychological and sexual Violence and Harassment through email, text, cartoons,
Guide to Developing a Cyber Security and Risk Mitigation Plan
www.cooperative.commanner. Security improvement does not happen overnight; it is a gradual process. This document describes security risks and recommends security controls in each of the following categories: People and policy security risks Operational security risks Insecure software development life cycle (SDLC) risks Physical security risks
Network Video Recorders User Manual - unv.ir
unv.irTo the maximum extent permitted by applicable law, the product described, with its hardware, software, firmware and documents, is ... product malfunction or information leakage caused by cyber attack, ... the terms IP camera and IPC refer to the same thing: network camera, which requires a connection to the network. And the
Violence Against Women: A State Level Analysis in India
ssi.edu.incyber bullying and many other forms of violence that is yet not being recognised. ... ( UNDP,2018). Adult women account for 51 per cent of all human trafficking victims detected globally. Nearly three out ... obtained from the reports of District Census Handbook of Andhra Pradesh (as per census 2011).
Electronic Medical Records in Healthcare
www.hhs.govFeb 17, 2022 · EMR/EHRs are valuable to cyber attackers because of the Protected Health Information (PHI) it contains and the profit they can make on the dark web or black market. These 18 identifiers provide criminals with more information than any other breached record. Extortion, fraud, identity theft, data laundering, Hacktivist /
www.dailypioneer.com Japan to invest 3.2L cr to boost ties ...
www.dailypioneer.comAhmedabad high-speed rail corridor. The announcement of the 42 billion dollar investment ... field of cyber security, capac-ity building, information shar-ing and co-operation after the
AR - eda.gov
eda.govCyber-Electric Security Training and Certification (CESTAC) CA ... The Rail Academy of Central California (TRACC) CA The NASDAQ OMX Entrepreneurial Center Inc. Milestone Mapping Circles to Accelerate Women Businesses CA The Regents of the University of …
Risk Management Program Rules - homeaffairs.gov.au
www.homeaffairs.gov.aurisk-based plan that outlines strategies and security controls as to how cyber and information security threats are being mitigated. 2. Responsible entities for critical infrastructure assets must, within 18 months of the commencement of this rule, ensure that their risk management program includes details of how
Weekly One Liners 14th to 20th of February 2022
wpassets.adda247.comBest IT Risk & Cyber Security Initiatives ... The cost of the ‘Rail-cum-Road-Bridge’ project is . Rs 696 crore. • Maharashtra’s. Health Minister, Rajesh Tope. has announced that Hope Express ó will be launched in the state to prevent cancer. This is the first such
भारतीय प्रौद्योगिकी संस्थान इंदौर
www.iiti.ac.in• Cyber security and cryptology • Computer architecture, operating systems and compilers ... or II AC rail fare, from the nearest city of their residence in India by the shortest route. The ticket for air travel should be booked from IRCTC or authorized Travel Agents
RULES COMMITTEE PRINT 117–35
rules.house.govdivision y—cyber incident reporting for critical infrastructure act of 2022 division z—israel relations normalization act of 2022 division aa—trans-sahara counterterrorism partnership program division bb—eb–5 reform and integrity act of 2022 division cc—burial equity for guards and reserves act
Manual Control Panel - Beckhoff Automation
download.beckhoff.comare equipped with security functions that support the secure operation of plants, systems, machines and networks. Despite the security functions, the creation, implementation and constant updating of a holistic security concept for the operation are necessary to protect the respective plant, system, machine and networks against cyber threats.
Minimum Cyber Security Standard - GOV.UK
assets.publishing.service.gov.uka) Users shall be given the minimum access to sensitive information or key operational services necessary for their role. b) Access shall be removed when individuals leave their role or the organisation. Periodic reviews should also take place to ensure appropriate access is maintained. 5 PROTECT Access to sensitive information and key
Fourth-Quarter 2021 PERFORMANCE REVIEW
s2.q4cdn.comsecurity threats, information technology or cyber-attacks, epidemics, sanctions or natural disasters; (22) work stoppages or other labor disruptions; (23) substantial pension and other postretirement benefit obligations; (24) potential environmental liabilities; and (25) effects of climate change and legal, regulatory or market responses to ...
Cyber Health Check Sample Report - IT Governance
www.itgovernance.co.ukIt is a basic cyber security principle that, without effective board-level cyber governance and risk management, organisations remain vulnerable to cyber attack. Actions that should be taken are:
CYBER CRIME - ICSI
www.icsi.eduLegal Protection against Cyber Crimes 42 4.1 Criminal Liabilities under Information Technology Act, 2000 42 4.2 Common Cyber Crimes and Applicable Legal Provisions: A Snapshot 71 4.3 Civil Liabilities under Information Technology Act, 2000 73 4.4 Civil Liability for Corporate: 79 4.5 Cyber Crimes under IPC and Special Laws 80
Cyber Security Assessment & Management (CSAM) - NIST
csrc.nist.govMay 26, 2021 · Cyber Security Assessment & Management (CSAM) Planning for Implementing SP 800- 53, Revision 5 May 26, 2021. Cybersecurity Services Staff. ... Planning For NIST SP 800-53, Revision 5 in CSAM. September 2020 NIST publishes SP 800-53, Revision 5 …
Cyber resilience oversight expectations for financial ...
www.ecb.europa.euInternational Organization of Securities Commissions (IOSCO) published the Guidance on cyber resilience for financial market infrastructures (Guidance) 1, which requires FMIs to immediately take the necessary steps to implement it, together with relevant stakeholders, to ensure that they enhance their levels of cyber resilience.
Cybersecurity Challenges - NIST
www.nist.govOct 18, 2018 · The Global State of Information Security ® Survey 2016 In a study of 200 corporate directors, 80% said that cyber security is discussed at most or all board meetings. However, two-thirds of CIOs and CISOs say senior leaders in their organization don’t view cyber security as a strategic priority. NYSE Governance Services and security vendor ...
Cyber-shot Handbook - Sony
www.sony.jpShutter speed = Length of time the camera receives light Aperture = Size of the opening allowing light to pass through ISO sensitivity (Recommended Exposure Index) = Recording sensitivity Exposure: 10 Basic techniques for better images Adjusting ISO Sensitivity (Recommended Exposure Index)
stations Visitor Center - National Park Maps
npmaps.com0 1 2 3 4 5 6 7 8 9 10 11 12 14 16 13 15 17 18 89 087 12 22 63 Road may be closed here during snow storms No trailers beyond this point BRYCE CANYON Creek NATIONAL ...
Similar queries
CYBER CRIME AND ITS CLASSIFICATION, Cyber, Cyber-terrorism, Assessment, Cyber Threat, Survey, Cyber security, Information, CYBER CRIME, Cyber terrorism, Financial, Oversight, Resilience, Expectations, Russia-Ukraine Conflict: Cyber and Information, Russia-Ukraine Conflict: Cyber and Information Warfare, Against, Violence, Cyber violence, Charter, State of Michigan, Michigan Cyber, Strategy, Michigan, Security, Cyber planning, Investigating and Prosecuting Cyber Crime, Crimes, Webelos, Boy Scouts of America, Scout, Cyber Chip, Scouts, Cyber Risk capabilities Cyber Strategy, Secure, Infrastructure, Maturity, Road, Enterprise Security Architecture, Planning, Pennsylvania, Charter school, Cyber charter school, School, FortiGate 100E, Middle East, Maritime, Maritime cyber risk, Risk, Plan, User Manual, Violence Against Women: A State Level Analysis, 2018, Handbook, Electronic, Fraud, Rail, Risk management, Cyber incident, Control, Automation, Systems, Minimum Cyber Security Standard, Organisation, Report, Protection, Laws, NIST, Cyber resilience oversight expectations for financial, International Organization of Securities Commissions, Cybersecurity Challenges, Cyber-shot Handbook, Length, National Park, BRYCE CANYON