Transcription of Vol. 8, No. 6, 2017 Security Issues in the Internet of ...
1 (IJACSA) International Journal of Advanced Computer Science and Applications,Vol. 8, No. 6, 2017 Security Issues in the Internet of things (IoT): AComprehensive StudyMirza Abdur RazzaqDepartment of Computer ScienceShah Abdul Latif UniversityKhairpur, PakistanSajid Habib GillDepartment of Computer ScienceNCBA & E Rahim Yar Khan CampusRahim Yar Khan, PakistanMuhammad Ali QureshiDepartment of Telecommunication EngineeringUniversity College of Engineering and TechnologyThe Islamia University of Bahawalpur, PakistanSaleem UllahDepartment of Computer Science & ITKhwaja Fareed University of Engineering and ITRahim Yar Khan, PakistanAbstract Wireless communication networks are highly proneto Security threats. The major applications of wireless commu-nication networks are in military, business, healthcare, retail,and transportations.
2 These systems use wired, cellular, or adhocnetworks. Wireless sensor networks, actuator networks, andvehicular networks have received a great attention in societyand industry. In recent years, the Internet of things (IoT) hasreceived considerable research attention. The IoT is consideredas future of the Internet . In future, IoT will play a vital roleand will change our living styles, standards, as well as businessmodels. The usage of IoT in different applications is expectedto rise rapidly in the coming years. The IoT allows billions ofdevices, peoples, and services to connect with others and exchangeinformation. Due to the increased usage of IoT devices, the IoTnetworks are prone to various Security attacks.
3 The deploymentof efficient Security and privacy protocols in IoT networks isextremely needed to ensure confidentiality, authentication, accesscontrol, and integrity, among others. In this paper, an extensivecomprehensive study on Security and privacy Issues in IoTnetworks is Internet of things (IoT); Security Issues in IoT; Security ; of things (IoT) has attracted considerable attentionduring the past few years. The concept of IoT was firstlyproposed by Kevin Ashton in 1999. Due to rapid advance-ments in mobile communication, Wireless Sensor Networks(WSN), Radio Frequency IDentification (RFID), and cloudcomputing, communications among IoT devices has becomemore convenient than it was before.
4 IoT devices are capableof co-operating with one another. The World of IoT includesa huge variety of devices that include smart phones, personalcomputers, PDAs, laptops, tablets, and other hand-held em-bedded devices. The IoT devices are based on cost-effectivesensors and wireless communication systems to communicatewith each other and transfer meaningful information to thecentralized system. The information from IoT devices is furtherprocessed in the centralized system and delivered to theintended destinations. With the rapid growth of communicationand Internet technology, our daily routines are more concen-trated on a fictional space of virtual world [1]. People canwork, shop, chat (keep pets and plants in the virtual worldprovided by the network), whereas humans live in the realworld.
5 Therefore, it is very difficult to replace all the humanactivities with the fully automated living. There is a boundinglimit of fictional space that restricts the future developmentof Internet for better services. The IoT has successfully in-tegrated the fictional space and the real world on the sameplatform. The major targets of IoT are the configuration ofa smart environment and self-conscious independent devicessuch as smart living, smart items, smart health, and smartcities among others [2]. Nowadays the adoption rate of theIoT devices is very high, more and more devices are connectedvia the Internet . According to appraisal [3], there are 30 billionconnected things with approximate 200 billion connections thatwill generate revenue of approximately 700 billion euros by theyear 2020.
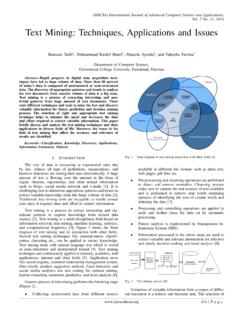
6 Now in China, there are nine billion devices that areexpected to reach 24 billion by the year 2020. In future, the IoTwill completely change our living styles and business will permit people and devices to communicate anytime,anyplace, with any device under ideal conditions using anynetwork and any service [4]. The main goal of IoT is to createSuperior world for human beings in future. Fig. 1 shows theconcept of IoT with their , the majority of these devices and appli-cations are not designed to handle the Security and privacyattacks and it increases a lot of Security and privacy issuesin the IoT networks such as confidentiality, authentication,data integrity, access control, secrecy, etc.
7 [5]. On every day,the IoT devices are targeted by attackers and intruders. Anappraisal discloses that 70% of the IoT devices are very easy toattack. Therefore, an efficient mechanism is extremely neededto secure the devices connected to the Internet against hackersand rest of the paper is organized as: Section II discussesIoT applications while Section III provides a brief overviewof Security requirements followed by Security threats in IoTare discussed in Section IV. Section V provides analysis ofdifferent attacks and their possible solutions and finally thepaper is concluded in Section | P a g e(IJACSA) International Journal of Advanced Computer Science and Applications,Vol. 8, No. 6, 2017 Internet of things (IoT)AnyBodyAnyOneAnyBusinessAnySe rviceAnyNetworkAnyPathAnyDeviceAnyThingA nyWhereAnyPlaceAnyContextAnyTimeFig.
8 Of APPLICATIONSThe main objectives of IoT are the configuration of a smartenvironment and self-conscious independent devices such assmart living, smart items, smart health, and smart cities amongothers [2]. The applications of IoT in industries, medical field,and in home automation are discussed in the following IoT in IndustriesThe IoT has provided a fair opportunity to build significantindustrial systems and applications [6], in an intelligent IoTtransportation system, the authorized person can monitor theexisting location and movement of a vehicle. The authorizedperson can also predict its future location and road earlier stage, the term IoT was used to identify uniqueobjects with RFID. Latterly, the researchers relate the termIoT with sensors, Global Positioning System (GPS) devices,mobile devices, and actuators.
9 The acceptance and services ofnew IoT technologies mainly depend upon the privacy of dataand Security of information. The IoT permits many things to beconnected, tracked and monitored so meaningful informationand private data collected automatically. In IoT environment,the privacy protection is a more critical issue as compared totraditional networks because numbers of attacks on IoT arevery IoT in Personal Medical DevicesThe IoT devices are also widely used in healthcare systemsfor monitoring and assessment of patients [7]. To monitorthe medical condition of a patient, Personal Medical Devices(PMDs) are either planted in patients body or it may attachto patients body externally. PMDs are small electronic devicesthat are becoming very common and popular.
10 The market valueof these devices is projected to be around17billion dollarsby2019[8]. These devices use a wireless interface to performcommunication with a base station that is further used to readstatus of the device, medical reports, and change parameters ofthe device, or update status on the device. Wireless interfacecauses a lot of Security and privacy threats for the patient. Thewireless interface of such devices is very easy to cyber-attacksthat may jeopardize the patients Security , privacy, and the case of health care, the primary goal is to ensure thesecurity of network in order to prevent the privacy of patientfrom malicious attacks. When attackers attack mobile devices,they have their predefined goals. Usually, their aim is to stealthe information, attack on devices to utilize their resources, ormay shut down some applications that are monitoring are many types of attacks on medical devices thatinclude eavesdropping in which privacy of the patient is leaked,integrity error in which the message is being altered, andavailability Issues which include battery draining attacks.