Search results with tag "Algorithm"
Tridiagonal Matrix Algorithm - Indian Institute of Space ...
www.iist.ac.inThomas’ algorithm, also called TriDiagonal Matrix Algorithm (TDMA) is essentially the result of applying gaussian elimination to the tridiagonal system of equations. The ith equation in the system may be written as a iu i 1 + b iu i + c iu i+1 = d i (2) where a 1 =0 and c N =0. Looking at the system of equations, we see that ith unknown can be
VDH Algorithm for Evaluating a Child with COVID-19 ...
www.vdh.virginia.govVDH Algorithm for Evaluating a Child with COVID-19 Symptoms or Exposure [This algorithm is for diagnostic purposes, and should not be used for screening testing] vdh.virginia.gov Send to School and/or Child Care Continue Normal Activities If quarantining and no symptoms develop, child may return to school and/or child care on Day 6.#§ Symptoms ...
EXAMPLE Machine Learning Exam questions
ibug.doc.ic.ac.ukGenetic Algorithm parameters need to be defined? What would be the suitable values of those parameters for the given problem? Provide a short explanation for each. What is the result of applying a single round of the prototypical Genetic Algorithm? Explain your answer in a clear and compact manner by providing the pseudo code of the algorithm.
Tridiagonal Matrices: Thomas Algorithm
www.industrial-maths.comTridiagonal Matrices: Thomas Algorithm W. T. Lee∗ MS6021, Scientific Computation, University of Limerick The Thomas algorithm is an efficient way of solving tridiagonal matrix syste ms. It is based on LU decompo-sition in which the matrix system Mx =r is rewritten as LUx =r where L is a lower triangular matrix and U is an upper triangular ...
多目的遺伝的アルゴリズムにおける各手法の比較
sys.ci.ritsumei.ac.jpthe results of Non-Dominated Sorting Genetic Algorithm-II (NSGA-II), Strength Pareto Evolutionary Algorithm-II (SPEA2), Master-Slave model with Local Cultivation model (MSLC) and Multi-Objective Genetic Algorithms with Distributed Environment Scheme (MOGADES). The comparison of each method is discussed through the numerical
CS 132 Compiler Construction
web.cs.ucla.edulearning algorithms algorithms graph algorithms union-find dynamic programming theory DFAs for scanning parser generators lattice theory for analysis ... – tree pattern matching – string pattern matching – dynamic programming 22. Back end errors IR machine code instruction selection register allocation
Mark scheme H446/02 Algorithms and programming …
www.ocr.org.ukand sorting algorithms; the material is generally accurate but at times underdeveloped. The candidate is able to apply their knowledge and understanding directly to the context provided although one or two opportunities are missed. Evidence/examples are for the most part implicitly relevant to the explanation.
4x4x4 Parity Algorithms - Speedsolving.com Wiki
www.cs.brandeis.edu4x4x4 Parity Algorithms - Speedsolving.com Wiki 12/17/17, 5(52 PM
Projected Gradient Algorithm
angms.scienceOct 23, 2020 · Q(:) is a function from Rnto Rn, and itself is an optimization problem: P Q(x 0) = argmin x2Q 1 2 kx x 0k2 2: I PGD is an \economic" algorithm if the problem is easy to solve. This is not true for general Qand there are lots of constraint sets that are very di cult to project onto. I If Qis a convex set, the optimization problem has a unique ...
2021 Obesity Algorithm FREE DOWNLOAD
obesitymedicine.orgInvestigational anti‐obesity agents 477 Top 10 takeaways: Microbiome 577 Top 10 takeaways: Anti‐obesity drug ... – Authors of the OMA Obesity Algorithm slides and eBook represent a diverse range of clinicians, allied health professionals, clinical researchers, and academicians, intended to reflect a multidisciplinary and balanced group of ...
Lecture 16: Mixture models - Department of Computer ...
www.cs.toronto.eduBe able to learn the parameters of a mixture model using the Expectation-Maximization (E-M) algorithm 2 Unsupervised learning So far in this course, we’ve focused on supervised learning, where we assumed we had a set of training examples labeled with the correct output of the algorithm. We’re going to
TECHNICAL INTERVIEW QUESTIONS - Computer …
allaboutcomputerprogramming.weebly.com“Data structures and Algorithms” by Weiss “Introduction to Algorithms” – Cormen • C/C++ Programming “Programming with C” – Byron Gottfried , Schaumm’s outline series “Principles of Programming Languages” by Robert W S ebesta , Addison Wesley “Programming with C++” – Balaguruswamy • Compiler Design
Programming External Flash with STM32 Devices - Keil
www.keil.comIn order to program on-chip or external flash, Keil MDK relies on flash programming algorithms – a special piece of software that the tool temporarily places into the MCU’s RAM and then uses its interface to supply the data and store it in the target flash memory. The flash algorithms for Keil MDK have the extension FLM. The Figure
Cache Replacement Algorithms Replacement algorithms …
zeus.cs.pacificu.eduAn on-chip cache reduces the processor's external bus activity. Further, an off-chip cache is usually desirable. This is the typical level 1 (L1) and level 2 (L2) cache design where the L2 cache is composed of static RAM. As chip densities have increased, the L2 cache has been moved onto the on-chip area and an additional L3 cache has been added.
Cluster Analysis: Basic Concepts and Algorithms
www-users.cse.umn.edu7 Cluster Analysis: Basic Concepts and Algorithms Clusteranalysisdividesdataintogroups(clusters)thataremeaningful,useful, orboth.Ifmeaningfulgroupsarethegoal ...
BEng in Computer Science - Hong Kong University of …
ugadmin.ust.hkCHEM 1004 Chemistry in Everyday Life 3 CHEM 1010 General Chemistry IA 3 CHEM 1020 General Chemistry IB 3 LIFS 1901 General Biology I 3 ... COMP 3711 Design and Analysis of Algorithms 3 COMP 3711H Honors Design and Analysis of Algorithms 4 2019-20 COMP (4Y) (2019-20 intake) Page 2.
Sorting algorithm - Saylor Academy
resources.saylor.org• General method: insertion, exchange, selection, merging, etc.. Exchange sorts include bubble sort and quicksort. Selection sorts include shaker sort and heapsort. • Adaptability: Whether or not the presortedness of the input affects the running time. Algorithms that take this into account are known to be adaptive. Stability
Fault Tree Analysis
www.cs.ucf.edulMore evaluation algorithms and codes were developed lA large number of technical papers were written on the subject (codes & algorithms) lUsage of FTA in the software (safety) community lAdopted by the Chemical industry
A Benchmark Comparison of Monocular Visual-Inertial …
rpg.ifi.uzh.chVIO algorithms, and there are several open-source software packages available that offer off-the-shelf visual pipelines that can be deployed on an end-user's system of choice. The current research literature offers some comparative results on the performance of the popular VIO algorithms, but these typically consider only a subset of the existing
Study of Machine learning Algorithms for Stock Market ...
www.ijert.orgAbstract: Stock market prediction is a very important aspect in the financial market. It is important to predict the stock market successfully in order to achieve maximum profit. This paper will focus on applying machine learning algorithms like Random Forest, Support Vector Machine, KNN and Logistic
Noisy intermediate-scale quantum (NISQ) algorithms
arxiv.orgNoisy intermediate-scale quantum (NISQ) algorithms Kishor Bharti, 1, ∗ Alba Cervera-Lierta, 2,3, Thi Ha Kyaw, Tobias Haug, 4 Sumner Alperin-Lea, 3 Abhinav Anand, 3 Matthias Degroote, 2,3,5 Hermanni Heimonen, 1 Jakob S. Kottmann, 2,3 Tim Menke, 6,7,8 Wai-Keong
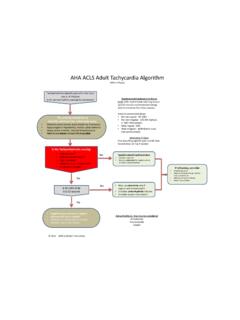
AHA ACLS Adult Tachycardia Algorithm
acls-algorithms.comAHA ACLS Adult Tachycardia Algorithm (With A Pulse) Tachyarrhythmia typically seen when the heart rate is . ≥ . 150/min. Is the tachyarrhythmia causing the symptoms? The priority should be to . identify and treat the underlying cause. Is the Tachyarrhythmia causing: • Hypotension? • Altered mental status? • Signs of shock? • Ischemic ...
1 Matrix multiplication: Strassen’s algorithm
www.web.stanford.edu1 a pointer to head of array A (i.e. pointer to smallest element in A) 2 b pointer to head of array B (i.e. pointer to smallest element in B) 3 while a;b are not null do 4 Compare the value of the element at a with the value of the element at b 5 if value(a) < value(b) then 6 add value of a to output C 7 increment pointer a to next element in A ...
B.Tech. in COMPUTER SCIENCE AND ENGINEERING (BTC-CSE ...
intranet.cb.amrita.eduENGG 19CSE302 Design and Analysis of Algorithms 3 0 3 4 ENGG 19CSE301 Computer Networks 3 0 3 4 ENGG 19CSE304 Foundations of Data Science 2 0 3 3 ENGG 19CSE303 Embedded Systems 3 0 3 4 ENGG Professional Elective I* 3 0 0 3 HUM 19SSK301 Soft Skills II 1 0 3 2 ENGG 19LIV390 Live-in –Labs*** [3]
METHODOLOGY FOR THE UNITED STATES POPULATION …
www2.census.govalgorithm may upset the consistency established in the controlling pro cess. To account for this, we use a variety of controlled rounding procedures (e.g., greatest mantissa or two-way controlled rounding). Base Population . The population estimates base is the starting point for each vintage of population estimates. Over rec ent
LSQR: An Algorithm for Sparse Linear Equations and …
web.stanford.edupseudoinverse of A. The relative precision of floating-point arithmetic is e, the smallest machine-representable number such that 1 + e > 1. 2. MOTIVATION VIA THE LANCZOS PROCESS In this section we review the symmetric Lanczos process [13] and its use in solving symmetric linear equations Bx = b.
Regulatory sandbox - FCA
www.fca.org.ukalgorithms in a regulatory sandbox. A sandbox coud al oll w a frim to make ther ai dvcie platform avaali ble to a lmi tied number of consumers. As a safeguard, once the advice is issued, but before transactions are executed, financial advisers …
Estimating Parameters of Van Genuchten Model for Soil ...
www.naturalspublishing.comcited in the literature [12,13]. Thus, the objective of this study was: (1) Improve the method of particle swarm optimization (IPSO) to avoid falling into local optimal solution and appearing the premature phenomenon; (2) Compare the performance of three intelligent algorithms, i.e. IPSO, GA and SA, on estimating the VG equation parameters for ...
HMM:隠れマルコフモデル - 東京大学
www.iba.t.u-tokyo.ac.jpEM(Expectation Maximization) ... θt+1 = θ* とする。t=t+1とする 4. Qが増大しなくなるまで、2,3を繰り返す. EM algorithm
An algorithm for managing warfarin resistance - ccjm
www.ccjm.orgwarfarin (Coumadin) to get their international normal-ized ratio (INR) into the therapeutic range. The cause of warfarin resistance can be either acquired (eg, poor compliance, drug interactions, dietary interactions) or hereditary, but the genetic mechanisms of warfarin resistance are not well understood. This review offers an
MC5301: ADVANCED DATA STRUCTURES AND …
www.dscet.ac.inMC5301 / Advanced Data Structures & Algorithms MCA 2018-2019 St. Joseph’s College of Engineering 6 11. What are the advantages in reverse polish (prefix and postfix notation) over polish (infix) notation? The advantages in prefix & postfix notation over infix notation is: The scanning of the expression is required in only one direction viz ...
Anemia Testing Algorithm - ARUP Consult
arupconsult.comanemia (including examination of peripheral blood smear for hypersegmented neutrophils); consider bone marrow examination Rule out blood loss and hemolysis Abbreviations Hb Hemoglobin MCV Mean corpuscular volume RBC Red blood cell Calculate corrected reticulocyte count Calculate corrected reticulocyte count.
Software Development
home.pearsonvue.com1.2 Construct and analyze algorithms and flowcharts to solve programming problems • Decision structures used in all computer programming languages; if ... Software Develpoment Principles 2.1 Describe software development lifecycle (SDLC) management • Requirement analysis, planning and design, implementation, testing,
SUGI 23: Querying the Data Warehouse with the SQL ...
support.sas.coma data warehouse as well as the various algorithms used in data summarizations. It provides a descriptive view, or ... matching of a column value to a defined set of values. The ... The LIKE condition selects rows from a table when a string search matches a …
Algorithms and Data Structures - 会津大学公式 ...
www.u-aizu.ac.jpthe search space where nodes and edges represents the states and the transitions respectively. For the 8 puzzle problem, a state (node) corresponds to an alignment sequence (permutation) of the pieces (including the empty space) and a transition corresponds to the movement of a piece. Generally, you can solve the problem by depth-first search and
Algorithms and Data Structures - u-aizu.ac.jp
u-aizu.ac.jp. . . . . .10/1 Analysis of Finding the Maximum We set up recurrence for Finding the Maximum. 1 [Divide] The divide step computes the middle of subarray, which takes constant time. Thus, O(1). 2 [Conquer] We recursively solve two subproblems, each of size n=2, which contributes 2T(n=2) to the running time. 3 [Combine] The comparison between two maximum values in two n …
Properties of Logarithms Worksheet - VealeyMath
vealeymath.weebly.comI) Model Problems For any positive numbers X, Y and N and any positive base b, the following formulas are true: log b X N = N • log b X Power Rule for Logarithms log b X Y § ©¨ · ¹¸ = log b X – log b Y Quotient Rule for Logarithms log b (XY) = logb X + log b Y Product Rule for Logarithms The following examples show how to expand logarithmic expressions using each of the
The laws of logarithms - mathcentre.ac.uk
www.mathcentre.ac.ukThe laws of logarithms mc-bus-loglaws-2009-1 Introduction There are a number of rules known as the lawsoflogarithms. These allow expressions involving logarithms to be rewritten in a variety of different ways. The laws apply to logarithms of any base but the same base must be used throughout a calculation.
Evaluating Logarithms
cdn.kutasoftware.comWorksheet by Kuta Software LLC Kuta Software - Infinite Precalculus Evaluating Logarithms Name_____ Date_____ Period____ Evaluate each expression. 1) log 2) log 3) log 4) log 5) log 6) log 7) log 8) log 9) log 10) log 11) log 12) log
Exponents and Logarithms Date Period
cdn.kutasoftware.comWorksheet by Kuta Software LLC Kuta Software - Infinite Precalculus Exponents and Logarithms Name_____ Date_____ Period____ Rewrite each equation in exponential form. 1) log 2) log 3) log 4) log Rewrite each equation in logarithmic form. 5) log 6) log 7) log
LOGARITHM TABLE (for numbers 1 to 5 - WikiEducator
wikieducator.orgLOGARITHM TABLE (for numbers 1 to 5.49) No. 0.00 0.01 0.02 0.03 0.04 0.05 0.06 0.07 0.08 0.09 1.0 0.000 0.004 0.009 0.013 0.017 0.021 0.025 0.029 0.033 0.037 1.1 0 ...
RATE LAW DETERMINATION OF CRYSTAL VIOLET …
cpb-us-e2.wpmucdn.comIntegrated rate laws, when arranged in line equation form, result in a mathematical function of concentration for the y axis and time on the x axis. The ... To solve for n, apply the rule of logarithms: (7) n = log (k 1/k
SYLLABUS for JEE (Main)-2021 Syllabus for Paper-1 (B.E./B ...
cdnbbsr.s3waas.gov.intrigonometric, exponential and logarithms functions. Integrations by substitution, by parts and by partial functions. Integration using trigonometric identities. Evaluation of simple integrals of the type ∫ × ë ë 2+ Ô 2, ∫ × ë √ ë 2, ∫ × ë, ∫ × ë 2− ë2 2, ∫ × ë Ô ë2+ Õ ë+ Ö,∫ × ë, ∫ ( ã ë+ ä) × ë
Similar queries
TriDiagonal Matrix Algorithm, TDMA, VDH Algorithm for Evaluating a Child with COVID, Algorithm, Child, Machine Learning, Genetic Algorithm, Tridiagonal, Tridiagonal matrix, Matrix, Genetic Algorithm-II, Genetic, Algorithms algorithms, Algorithms, Matching, String, 4x4x4 Parity Algorithms - Speedsolving, Projected Gradient Algorithm, Optimization, Convex, 2021 Obesity Algorithm, Microbiome, Health, Expectation-Maximization, TECHNICAL INTERVIEW QUESTIONS, Data structures and Algorithms, Programming, Programming algorithms, Data, Cache Replacement Algorithms Replacement algorithms, Cache, L3 cache, BEng in Computer Science, In Everyday Life, Sorting algorithm, General method, Software, Study of Machine learning Algorithms for Stock Market, Stock market, Market, AHA ACLS Adult Tachycardia Algorithm, Pulse, Matrix multiplication: Strassen’s algorithm, Pointer, Foundations, Algorithm for Sparse Linear Equations and, Pseudoinverse, Regulatory sandbox, Objective, Expectation Maximization, EM algorithm, An algorithm for managing warfarin, Ccjm, Warfarin, Of warfarin, DATA STRUCTURES AND, Data Structures, Anemia Testing Algorithm, Anemia, Algorithms and Data Structures, Search, Puzzle, Properties of Logarithms, Formulas, The laws of logarithms, The lawsoflogarithms, Logarithms, Laws, Worksheet, LOGARITHM TABLE for numbers 1, Of logarithms