Attacks
Found 9 free book(s)Speculative Buffer Overflows: Attacks and Defenses
people.csail.mit.eduSpeculative Buffer Overflows: Attacks and Defenses Vladimir Kiriansky vlk@csail.mit.edu Carl Waldspurger carl@waldspurger.org Abstract Practical attacks that exploit speculative execution can leak
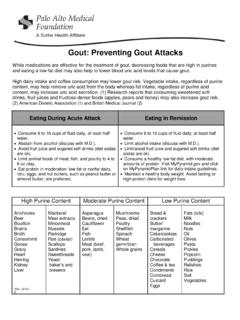
Gout: Preventing Gout Attacks
www.pamf.orgGout: Preventing Gout Attacks While medications are effective for the treatment of gout, decreasing foods that are high in purines and eating a low-fat diet may also help to …
When the Enemy Attacks: It Is Written… - Times Of Refreshing
www.timesofrefreshing.comWhen the Enemy Attacks: It Is Written… 1. Isaiah 54:14 – In righteousness I am established, I am far from oppression, for I shall not fear; and from terror,
AMA Attacks Physicians Caring for Their Families
jpands.orgThemostimportantpeopleinthelivesofmostphysiciansare their spouses, children, parents, and siblings—their immediate families. These are the very people who have ...
PERFORMANCE OF NOMEX MILITARY UNIFORMS IN …
www.dtic.milAFRL-ML-TY-TR-2007-4520 PERFORMANCE OF NOMEX® MILITARY UNIFORMS IN ATTACKS BY FLAME FIELD EXPEDIENT WEAPONS – A LITERATURE STUDY Ramon D. …
Cybersecurity regained: preparing to face cyber attacks - EY
www.ey.com20th Global Information Security Survey 2017-18 1 Paul van Kessel EY Global Advisory Cybersecurity Leader Welcome Welcome to the 20th EY Global Information Security Survey (GISS) exploring the
The 9/11 Commission Report
www.9-11commission.govList of Illustrations and Tables ix Member List xi Staff List xiii–xiv Preface xv 1. “WE HAVE SOME PLANES” 1 1.1 Inside the Four Flights 1
Time cures everything, but there are Bayonne, New Jersey
www.911monument.comTHE MEMORIAL AT HARBOR VIEW PARK Bayonne, New Jersey Time cures everything, but there are things we cannot and must not forget. Standing more than 100 feet tall,
U.N. Peacekeeping: Few Successes, Many Failures, Inherent ...
www.idppcenter.com! 3! Olusegun!Obansanjo,!then!President!of!Nigeria,!successfully!led!African!diplomatic!efforts! thatresultedinLiberianPresidentCharlesTaylora ...