Search results with tag "Attacks"
Examples of Terrorist Attacks Domestic Terrorist Attacks ...
training.fema.govInternational Terrorist Attacks: October 14, 2002. Bali, Indonesia. Bombing of the Sari Club. Deaths: near 200, including 2 Americans; injuries: over 300, including four Americans. “An estimated 20,000 Americans are in Indonesia at any one time, although relatively few are permanent residents. They range from tourists to employees of large
Marvell 88Q4364 Automotive 802.3ch compliant 10GBase …
www.marvell.comimplements the Ethernet physical layer portion of 2.5G/5G/10GBASE-T1 as defined by the IEEE 802.3ch standard. The 88Q4364 has integrated MACsec that secures against the Layer 2 In-Vehicle Networking security threats. MACsec secures data exchange on a hop-by-hop basis and prevents attacks such as intrusion, man-in-the-middle, and replay attacks.
What are Panic Attacks? - Therapist Aid
www.therapistaid.comThe symptoms of panic typically peak within 10 minutes, and end within 30 minutes. However, some lingering symptoms can last over an hour. Panic attacks can seem to occur randomly, or they can be closely linked to a specific source of anxiety such as driving, crowded places, or simply leaving home.
A Classification of SQL Injection Attacks and …
www.cc.gatech.eduSQL injection refers to a class of code-injection attacks in which data provided by the user is included in an SQL query in such a way that part of the user’s input is treated as SQL code. By lever-Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are
Public-Key Cryptography RSA Attacks against RSA - LRI
www.lri.frDecryption attacks on RSA • RSA Problem: Given a positive integer n that is a product of two distinct large primes p and q, a positive integere suchthatgcd(e, (p-1)(q-1))=1, and an integer c, find an integer m such that me≡c (modn) – widely believed that the RSA problem is computationally equivalent to integer factorization;
MARAUDING TERRORIST ATTACKS - GOV.UK
assets.publishing.service.gov.uk1 CPNI guidance on completing a risk assessment: https://www.cpni .gov.uk/principles-risk-assessment 2 Report on live simulations, available from your CPNI adviser: “ ASCEND – Improving Organisational Response to Marauding Terrorist Attacks: A Summary of Key Emerging Themes from Trials Conducted in 2017 and Early 2018” The risk to your organisation
CARDIOVASCULAR DISEASES - World Health Organization
www.who.intwill help to prevent heart attacks and strokes. Eating at least five servings of fruit and vegetables a day, and limiting your salt intake to less than one teaspoon a day, also helps to prevent heart attacks and strokes. To maintain an ideal body weight, take regular physical activity and eat a healthy diet. 1 Stop tobacco use
Introduction to TCP/IP Network Attacks
seclab.cs.sunysb.eduIntroduction to TCP/IP Network Attacks Guang Yang sunlight@cs.iastate.edu Department of Computer Science Iowa State University Ames, IA 50011 ABSTRACT Computation model has experienced a significant change since the emergence of the
Multi-Expert Adversarial Attack Detection in Person Re ...
openaccess.thecvf.comtions, Wang et al. [45] implemented robust physical-world attacks against deep ReID for generating adversarial pat-terns on clothes, which learns the variations of image pairs 15098. o ao Query -Support Relation o bo Support -Support Relation o co Cross -Expert Relation
Guide to Effective Remediation of Network Vulnerabilities.…
www.qualys.comdays after news announcements of vulnerabilities Attacks have dramatically accelerated damage by using sophisticated technology for automatic replication, pre-identification of vulnerable hosts, and targeting ... These threats are also emerging faster than ever. In the past, the discovery/attack
Steps to Freedom in Christ
9270d3bbcc2624c4616b-98bed3fa049b73fdf4c7dab84c8c07a5.r33.cf2.rackcdn.comand Satan. Only God is all-powerful, always present and all knowing. Satan was defeated by Christ the Victor at the cross, so don’t believe the lie that your situation is hopeless or that you are helpless against the devil’s attacks. Satan knows you have authority over him in Christ, but he doesn’t want you to know it. He is a liar and ...
Panic/Anxiety Attacks: Identification and Self-help Strategies
www.mcgill.ca6. Use Positive Self-Statements Write out and, at the initial stages of the panic attack, begin to repeat some positive coping statements in your mind. You can use a single phrase or combination of statements, depending on what is successful for you. Use those statements that are most relevant to you and your symptoms. Some common positive coping
Types of Hacking Attack and their Counter Measure
www.ripublication.comTypes of Hacking Attack and their Counter Measure Minakshi Bhardwaj and G.P. Singh Galley discusses three types of attacks against computer systems: Physical, Syntactic and Semantic. A physical attack uses conventional weapons, such as bombs or fire. A syntactic attack uses virus-type software to disrupt or damage a computer system or network.
The 2017 Attacks: What needs to change? - GOV.UK
assets.publishing.service.gov.ukthe Joint Intelligence Organisation and the National Security Secretariat in the Cabinet Office; Defence Intelligence in the Ministry of Defence; and the Office for Security and Counter-Terrorism in the Home Office. The Committee consists of nine Members drawn from both Houses of Parliament. The Chair is elected by its Members.
Ouroboros: A Provably Secure Proof-of-Stake Blockchain ...
eprint.iacr.orgof physical resources (e.g., proof of work). We also present a novel reward mechanism for in-centivizing proof of stake protocols and we prove that, given this mechanism, honest behavior is an approximate Nash equilibrium, thus neutralizing attacks such as selfish mining. We also
Screen for Child Anxiety Related Disorders (SCARED) …
www.aacap.org30. My child is afraid of having anxiety (or panic) attacks. 31. My child worries that something bad might happen to his/her parents. 32. My child feels shy with people he/she doesn’t know well. 33. My child worries about what is going to happen in the future. 34. When my child gets frightened, he/she feels like throwing up. 35.
Action for Diabetes - NHS England
www.england.nhs.ukDiabetes doubles the risk of cardiovascular disease (heart attacks, heart failure, angina, strokes).7 Diabetes is the most common reason for end stage kidney disease and the most common cause of blindness in people of working age.8 Up to 100 people a week have a limb amputated as a result of diabetes, and in
UNDERSTANDING DOMESTIC VIOLENCE
www.futureswithoutviolence.org4. A combination of physical attacks, terrorist acts, and controlling tactics used by perpetrators that result in fear as well as physical and psychological harm to victims and their children. 5. A pattern of purposeful behavior, directed at achieving compliance from or …
2021 NSA Cybersecurity Year in Review
media.defense.govFeb 03, 2022 · even saw how ransomware attacks can restrict our travel and resources and secure our systems, but also to create technical affect our food supply chain. It hit home that cybersecurity is guidance that helps others secure their systems at scale. national security. Since the standup of NSA’s Cybersecurity Directorate in 2019,
The Response to Hurricane Katrina
irgc.orgHurricane Katrina occurred four years after the attacks of 9/11, three years after the subsequent creation of the Department of Homeland Security (DHS), and one year after the DHS had created a National Response Plan. But despite the heightened attention to homeland security, the response to Katrina was a failure.
CRYPTOGRAPHY AND NETWORK SECURITY - Tamilnadu
www.sasurieengg.comfacilities. Another form of service denial is the disruption of an entire network, either by disabling the network or overloading it with messages so as to degrade performance. It is quite difficult to prevent active attacks absolutely, because to do so would require physical protection of all communication facilities and paths at all times.
The Screwtape Letters Study Guide and Commentary Letters 1 …
screwtapestudyguide.comWe are not left guessing at the proper way to be equipped against spiritual attacks. After Jesus fasted for forty days and nights in the wilderness, it is recorded that Satan continued his series of temptations against Him (Matthew 4:1-11; Luke 4:1-13). Jesus’ response to these three recorded
USD(R&E) Strategic Vision and Critical Technology Areas
www.cto.milcomplex, ranging from sophisticated cyber-attacks to supply chain risks, and from defending against hypersonic missiles to responding to biological threats. In an ever shifting and fast moving global environment, technological advantage is not stagnant and the Department cannot
S ubmarines | Nonfiction Reading Test 1
www.ereadingworksheets.comto great effect. Though the Japanese attack on Pearl Harbor destroyed or severely damaged many of the U.S. Navy’s front-line Pacific Fleet ships, U.S. submarines survived the attack and went on to cause great damage. Submarines, though only about 2 percent of the U.S. Navy, destroyed over 30 percent of the Japanese Navy. This made U.S.
NAACCR RECOMMENDED ABBREVIATION LIST ORDERED BY …
www.umc.eduWORD/TERM(S) ABBREVIATION/SYMBOL Sacral vertebra S1-S5 Salpingo-oophorectomy SO Satisfactory SATIS Serum glutamic oxaloacetic transaminase SGOT ... Transient ischemic attack TIA Transitional cell carcinoma TCC Transurethral …
BHF UK CVD Factsheet - British Heart Foundation
www.bhf.org.ukCoronary heart disease (CHD) is the most common type of heart and circulatory disease. It occurs when coronary arteries become narrowed by a build-up of atheroma, a fatty material within their walls. The pain or discomfort felt from such narrowing is called angina and if a blockage occurs it can cause a myocardial infarction (heart attack). Key ...
First aid fact sheet Heart attack - St John Ambulance ...
stjohn.org.auThe warning signs of heart attack vary. Symptoms can start suddenly, or develop over time and get progressively worse. People can have just one symptom or a combination of symptoms. The patient can feel discomfort or pain in the centre of the chest. This chest pain can: • start suddenly, or slowly over minutes
Air Force Doctrine Publication 3-70,
www.doctrine.af.milAir Force Doctrine Publication 3-70, Strategic Attack 4 strikes. By whichever means, against any enemy, SA aims to produce strategic, war-winning effects more …
Crim Attack Outline - NYU School of Law
www.law.nyu.eduComes in only for violations/statutory rape for very young children (under 10); left some room for drafters to add these offenses. • Common law: strict liability gets at the concept of notice: • Generally invoked in the context of public welfare offenses (offenses where social utility outweighs what potentially innocent
ANNE FRANK - United States Holocaust Memorial Museum
www.ushmm.orgsurprise attack on the US Pacific fleet at Pearl Harbor, Hawaii. The United States declared war on Japan. On December 11, Nazi Germany declared war on the United States. The United States officially entered World War II and joined the Allies. ANNE FRANK
Salt Attack and Rising Damp Technical Guide
www.environment.sa.gov.auSalt attack is the decay of masonry materials such as stone, brick and mortar by soluble salts forming crystals within the pores of the masonry. As the salt crystals grow the masonry is disrupted and decays by fretting and loss of surface skins. …
RU L ES REFERENC E - Fantasy Flight Games
images-cdn.fantasyflightgames.comAttack range is the range at which a squadron or a ship’s hull zone can perform an attack as determined by the armament it is using. • A hull zone’s maximum attack range is close range if it has only black dice in its armament, medium range if it has at least one blue die, or long range if it has at least one red die.
CWA History: A Brief Review - Communications Workers of ...
www.cwa-union.orgIn December 1941, following the attack on Pearl Harbor, the AFL and CIO voluntarily gave no-strike pledges to the federal government for the duration of the war. In January, 1942, President Roosevelt created the National War Labor Board (NWLB). The NWLB was charged with settling all disputes between labor and management that threatened war ...
Pet Battles Cheat Sheet - WarcraftPets.com
www.warcraftpets.comwith every successful attack. Magic: Cannot lose more than 35% of their max health at once. Mechanical: Comes to life once per battle to 25% health. Undead: Comes back to life for 1 round when killed. Use Against Don't Use Against Bonus Strike +50% O o O e O Bonus Defense +33% o o 0 e o o Weak Strike -33% O O O O O O Weak Defense -50% O O e O O O O
U.S. Marine Aviation in Korea - United States Marine Corps
www.marines.milAttack Squadron 323 on 30 June 1952) (Vought F4U Corsair, Vought AU-i Corsair) Marine Attack Squadron 332 (Vought F4U Corsair) Marine …
UDL Strategies to Provide Specially Designed Instruction ...
f.hubspotusercontent00.netimproving word attack skills Kinesthetic Learning • Dancing while reading/ decoding • Counting syllables using manipulatives • Using arm strategy or other physical prompt to blend/segment words • Embedded Instruction: • Look for naturally occurring opportunities to target decoding skills, comprehension skills, and/or
My entity just experienced a cyber-attack! What do we do now?
www.hhs.govof a cyber-attack or similar emergency an entity: Must execute its response and mitigation procedures and contingency plans. ii. For example, the entity should immediately fix any technical or other problems to stop the incident. The entity should also take steps to mitigate any impermissible disclosure of protected health information, iii
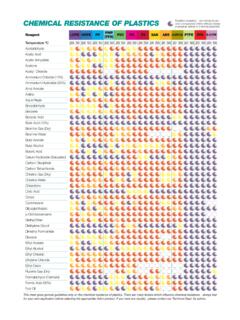
CHEMICAL RESISTANCE OF PLASTICS
hcs-lab.comchemical properties. Good general resistance - minor attack may occur after long periods of storage. Limited resistance - product can be used for brief mixing and measuring. Poor resistance - product becomes unstable on contact with chemical. Clear LDPE HDPE PP PMP (TPX) PVC PC PS ACRYLIC (AC) PTFE PFA NO-50 NO-100 YES-20* YES-180 NO-25 YES …
Transient Ischaemic Attack (TIA) / Stroke Clinical Pathway ...
www.health.qld.gov.auAdmit / refer Stroke Unit See local or national stroke management guidelines for further details Non-contrast CT Brain If CT: bleed, refer as appropriate If CT: Ischaemia / NAD, Risk Stratify the TIA (see over)?Thrombolysis Candidate Contact Stroke, Medical or ED consultant urgently re: acute imaging See Statewide or local Thrombolysis protocol for
Similar queries
Terrorist Attacks, Marvell 88Q4364 Automotive, Compliant 10GBase, Physical, Attacks, What are Panic Attacks, Therapist Aid, Symptoms, Classification of SQL Injection Attacks and, Class, Marauding Terrorist Attacks, Guidance, World Health Organization, Heart attacks and strokes, Introduction, TCP/IP, Robust physical, World attacks, Vulnerabilities, Vulnerabilities Attacks, Threats, Steps to Freedom, Satan, Panic/Anxiety Attacks, Identification, Self, Types of Hacking Attack and, Computer, The 2017 Attacks: What needs to change, Organisation, Ouroboros, For Child Anxiety Related Disorders SCARED, Anxiety, Panic, Action for Diabetes, Heart attacks, Heart, Strokes, UNDERSTANDING DOMESTIC VIOLENCE, Terrorist, Psychological, Supply chain, Hurricane Katrina, Network, Defending against, S ubmarines | Nonfiction Reading Test 1, Attack, Pearl Harbor, WORD, Myocardial infarction heart attack, Crim Attack, Statutory, ANNE FRANK, United States Holocaust Memorial Museum, Salt Attack and Rising Damp, Squadron, CWA History: A Brief Review, Pet Battles Cheat Sheet, United States Marine Corps, Attack Squadron, Word attack skills, Skills, CHEMICAL RESISTANCE, Chemical, Resistance, Transient Ischaemic Attack (TIA) / Stroke Clinical Pathway, Stroke, Protocol