Firewall through
Found 6 free book(s)Sophos XG Firewall
www.sophos.comgeneration firewall but often challenging to implement in a seamless and transparent way. Synchronized User ID eliminates the need for client or server authentication agents by sharing user identity between the endpoint and the firewall through Security Heartbeat. It’s just another great benefit of having your firewall and endpoints
Configuring IP Passthrough - AT&T
www.att.com- Select the Firewall tab from the Web Management page. Firewall page displays status of system firewall elements. - Select the IP Passthrough option by selecting the IP Passthrough or Disabled option from the drop-down menu to activate or deactivate IP Passthrough. - After the desired setting is achieved, click on the Save button.
IPSec, VPN, and Firewall Concepts
www.cs.unh.eduAppendix B IPSec, VPN, and Firewall Concepts Overview: VPN Concepts B-6 Using Monitoring Center for Performance 2.0.1 78-16217-02 MD5 Message Digest 5 The result of a co mputation that provides basic message authentication. NAS Network Access Server Gateway that connects asynchronous devices to a LAN or WAN through network and terminal emulation
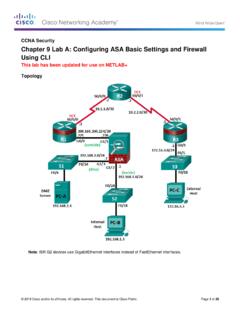
Chapter 9 Lab A: Configuring ASA Basic Settings and ...
www.ccri.eduIn Parts 2 through 4 you will configure basic ASA settings and the firewall between the inside and outside networks. In part 5 you will configure the ASA for additional services, such as DHCP, AAA, and SSH. In Part 6, you will configure a DMZ on the ASA and provide access to …
Opening a Case With TAC - Cisco
www.cisco.combehind a firewall. Using an external proxy machine, the system relays TCP/IP communications from behind your firewall to a host behind another firewall at the Cisco Technical Assistance Center (TAC). Using this relay server maintains the integrity of both firewalls while supporting secure communication between the shielded remote systems.
Top 10 Tips for Cybersecurity in Health Care
www.healthit.govsoftware will help to find and destroy malicious softwar e that has already entered, a firewall's job is to prevent intruders from entering in the first place. In short, the anti-virus can be thought of as infection control while the firewall has the role of disease prevention. A firewall can take the form of a software product or a hardware ...