Search results with tag "Sensitive"
Phase sensitive detection: the lock-in amplifier
www.phys.utk.eduand phase-sensitive capabilities may put you on a fruitful track. B. Phase sensitive detection A lock-in, or phase-sensitive, amplifier is simply a fancy AC voltmeter. Along with the input, one supplies it with a periodic reference signal. The amplifier then responds only to the portion of the input signal that occurs at the reference frequency
VMW Tuning Latency Sensitive Workloads - VMware
www.vmware.comLatency-Sensitive Workloads in vSphere Virtual Machines vNUMA is automatically enabled for VMs configured with more than 8 vCPUs that are wider than the number of cores per physical NUMA node. For certain latency-sensitive workloads running on physical hosts with fewer than 8 cores per physical NUMA node, enabling vNUMA may be beneficial.
Implementing Rules and Regulations of Republic Act No ...
officialgazette.gov.ph54. Improper Disposal of Personal Information and Sensitive Personal Information 55. Processing of Personal Information and Sensitive Personal Information for Unauthorized Purposes 56. Unauthorized Access or Intentional Breach 57. Concealment of Security Breaches Involving Sensitive Personal Information 58. Malicious Disclosure 59.
All Sections Must Be Completed Time Sensitive documents …
sos.oregon.govTime Sensitive documents - We highly recommend the use of expedited shipping through Federal Express or UPS . for time sensitive and valuable documents requiring an authentication or apostille. Other forms of mail, including U.S. Postal Service "Express or Priority Mail" DO NOT
TRANSPORTATION OF FREIGHT - U.S. Department of Defense
media.defense.govMar 28, 2017 · MOVEMENT OF SENSITIVE CONVENTIONAL AA&E, CLASSIFIED (SECRET AND CONFIDENTIAL), AND CCI SENSITIVE ITEMS ... H. Small Shipments of Arms Ammunition and Explosives (AA&E) 5-3 I. Security Plan and Training 5-5 ... Appropriate in-transit physical and security protection measures are used to meet mission
Mohawk EnPress - Aladdin Commercial
cdn.aladdincommercial.comAbout EnPress ® EnPress® pressure sensitive adhesive is nonflammable and has low odor and “zero” calculated VOC’s, which makes it ideal for use in schools, healthcare facilities, public buildings, and anywhere odor is a concern. EnPress® pressure sensitive adhesive is CRI Green Label Plus ™ approved. This adhesive
(U) SENSITIVE COMPARTMENTED INFORMATION …
www.dni.gov(U) SENSITIVE COMPARTMENTED INFORMATION NONDISCLOSURE AGREEMENT. An Agreement between _____ _____ and the United States. (Name – Printed or Typed) 1. (U) Intending to be legally bound, I hereby accept the obligations contained in this Agreement in consideration of my being granted
NHS Foundation Trust Meticillin- Sensitive Staphylococcus ...
www.bfwh.nhs.ukMeticillin-sensitive Staphylococcus aureus is a type of bacteria (germ) which lives harmlessly on the skin and in the noses, in about one third of people. People who have MSSA on their bodies or in their noses are said to be colonised. However MSSA colonistation usually causes them no problems, but can cause an infection when it
Cognizant Candidate Privacy Statement
www.cognizant.comSensitive Personal Information - We do not require you to provide any Sensitive Personal Information during the recruitment process. Nonetheless, should you be successful for a role, we –where permitted by applicable law- may then
Nutrition Targets and Indicators for the - UNSCN
www.unscn.orgNutrition Targets and Indicators for the ... disease, impairs quality of life, and acts as a brake on economic growth worldwide. In this sense, ... of scaling up direct nutrition actions and also provides new information on “nutrition-sensitive” interventions [11]. Nutrition-sensitive interventions span a variety of sectors and address ...
T20WC PRIVACY POLICY
d35kvm5iuwjt9t.cloudfront.netJul 02, 2021 · • other sensitive information about you (for example, information about your racial or ethnic origin or that of your parents). Sensitive information is afforded a higher level of privacy protection than other personal information. The T20WC Entities may use health information about you for insurance purposes and/or to ensure
An Empirical Lower Bound on the Overheads of Production ...
arxiv.org3) When optimizing for latency-sensitive workloads, such as lusearch, Shenandoah seems better suited because of shorter pause times1 (Fig. 2a). However, Shenandoah ends 1The distribution of the pause times is more appropriate for latency-sensitive workload. The average pause time is used here for the simplicity of illustration.
ICD 705 Physical Security Construction Requirements for SAP
www.cdse.eduSensitive Compartmented Information (SCI) Administrative Security Manual: Administration of Physical Security, Visitor Control and ... Standards of the Accreditation and Reciprocal Use of Sensitive Compartmented Information Facilities ... and procedural security information including facility entrances and emergency exits, intrusion
COOKING AND ITS EFFECT ON NUTRITION
www.acsedu.co.ukThe water soluble vitamins, including Vitamin C and B-complex vitamins, are heat sensitive (heat-labile) and easily destroyed by blanching so care must be taken not to blanch foods for too long and to quickly refresh foods in cold water to prevent heat labile nutrients from being destroyed. Braising
The Business Case for Higher Levels of Nurse Staffing in ...
www.nursingworld.orgavailable evaluations of nurse staffing and patient outcomes published between 2000 and 2016. Avalere developed a simple, Microsoft® Excel (2013)-based cost calculator to measure the impact on hospital budgets of reductions in five nursing-sensitive quality indicators through adjustments to nurse staffing.
CHCDIS007 Facilitate the empowerment of people with …
aspire-solidus-production.s3-ap-southeast-2.amazonaws.comwill not reveal any sensitive or confidential business information relating to that organisation. This may include individualised service plans, profit or loss amounts,
MCO P5530.14 MARINE CORPS PHYSICAL SECURITY …
www.mccsmcrd.comseparates recommended physical security measures from required measures and eliminates conflicting guidance. 3. Identifies physical security requirements that are not covered by other specialized security programs. Protection of classified material, automated data processing (ADP) systems, and sensitive conventional arms,
FR09/2021 Environmental, Social and Governance (ESG ...
www.iosco.orgChapter 1: Product and Market Overview ... of transparency, and handling confidential information. The recommendations also suggest ... Indeed, as investors become more sensitive to the potential financial risks posed by climate change and the potential impact of other ESG , such considerations
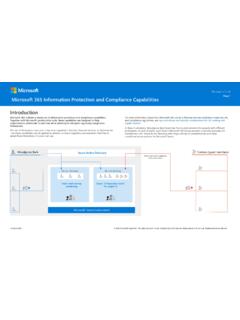
Page 1 Microsoft 365 Information Protection and Compliance ...
download.microsoft.comThe following illustration demonstrates DLP enforcing policies for data that matches several sensitive information types (Policy 1) and data labeled ‘Highly Confidential’ (Policy 2). We see that if an attempt is made to share data marked ‘Highly Confidential’ outside of allowed recipients, DLP blocks the sharing
GLUTEN SENSITIVE DINNER MENU - Patsy's American
www.patsysamerican.comSeafood Tower*...12 oysters, 6 clams, 6 shrimp, smoked mussels & 1/2 Maine lobster served with blood orange mignonette & Grand Marnier aioli...79 The Triple Decker* ...18 oysters, 9 clams, 9 shrimp, mussels, tuna tartare & a one pound
Guide to Intrusion Detection and Prevention Systems ... - NIST
nvlpubs.nist.govinformation technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series
By design: urban design in the planning system: towards ...
www.designcouncil.org.ukPrinted in Great Britain on material containing 75% post-consumer waste and 25% ECF pulp. Month 2000. ... streets and public spaces that are safe, accessible, pleasant to use ... l a sensitive response to the local context; l judgements of what is feasible in terms of
Information that requires protection. - Archives
www.archives.gov- Enhanced physical safeguards - Limits on who can access the information Laws, Regulations, or Government-wide policies ... – Attempting to enter or access to sensitive areas (where CUI is stored, discussed, or ... Controlled Unclassified Information (CUI) Program Author: C² Technologies, Inc.
Lever-Type Dial Indicators DIAL TEST INDICATORS
www.mitutoyo.comLever-Type Dial Indicators. DIAL TEST INDICATORS. B. ulletin No. 2232. SMALL TOOL INSTRUMENTS . AND DATA MANAGEMENT. 2 • A ø8mm (ø0.315 in) plain stem ... Longer styli for the most sensitive indicators allow access to difficult-to-measure features. L. 1. 0.001mm graduation models: L. 2. now 15.2mm, was 11.2mm 0.002mm graduation models: L. 2.
Quality Indicators Sensitive to Nurse Staffing in Acute ...
www.ahrq.govQuality Indicators for Nurse Staffing 377 Measures of quality in health care are generally accepted as those indicators representing structure, process, and/or outcomes.2, 14 It is unclear, however, whether there is consistency in how quality is defined and measured across
Cyber Essentials: Requirements for IT infrastructure
www.ncsc.gov.ukorganisation’s sensitive information — often with ease. By applying some simple technical controls when installing computers and network devices you can minimise inherent vulnerabilities and increase protection against common types of cyber attack. Requirements under this technical control theme Computers and network devices
GUIDELINES FOR MANAGEMENT OF SANITARY WASTE
cpcb.nic.inGuidelines, 2017 Swachh Bharat Mission Gramin (SBM-G) is sensitive to menstrual hygiene needs of adolescent girls and women. Towards this end, guidelines on Menstrual Hygiene Management have been issued by the Ministry of Drinking Water & Sanitation in 2015 and must be adhered to. The
DoD 5200.01, Vol. 3, February 24, 2012 - LSI Education
lsieducation.comsensitive compartmented information (SCI), and Special Access Program (SAP). This guidance is developed in accordance with Reference (b), Executive Order (E.O.) 13526, E.O. 13556, and part 2001 of title 32, Code of Federal Regulations (CFR) (References (d), (e), and (f)). This combined guidance is known as the DoD Information Security Program. b.
HIGHLIGHTS OF PRESCRIBING INFORMATION Platinum …
www.pi.amgen.comPlatinum-sensitive recurrent epithelial ovarian, fallopian tube, or primary peritoneal cancer (2.7) • 15 mg/kg every 3 weeks with carboplatin and paclitaxel for 6-8 cycles, ... demonstrating that it is highly similar to an FDA-approved biological product,
SOMATOM Force Get two steps ahead with Dual Source CT
cdn0.scrvt.comsensitive StellarInfinity detectors, SOMATOM Force is the ideal scanner for high-speed, large-volume coverage at outstanding image quality. Improve patient care Kidney-friendly scanning: SOMATOM Force allows you to routinely perform exams at 70-90 kV, even with adults. This may reduce the quantity of contrast media required.
SPECIAL OPERATIONS - U.S. Air Force Doctrine
www.doctrine.af.milFeb 01, 2020 · adaptable force capable of operating in dynamic environments. AFSOF can: Deploy rapidly to provide tailored responses to different situations. Gain access to hostile, denied, or politically sensitive areas to prepare the operational environment for future operations and develop asymmetric options for addressing ambiguous situations.
Privacy Policy - Programmed
www.programmed.com.auThis privacy policy outlines how Programmed manages Personal Information, including the type of information, how it is collected ... Sensitive Information ’ is a subset of Personal Information - about an individual’s racial or ethnic origin; political opinions;
DATA PRIVACY POLICY - Capgemini
www.capgemini.comand Sensitive Personal Data or Information) Rules which deals with practices and procedures for protection and maintenance of Personal Information. It is Capgemini Group’s policy to comply with the privacy legislation within each jurisdiction in which a Capgemini entity operates. The privacy legislation and/or
Department of Defense MANUAL
www.esd.whs.milCompartmented Information and Security Policy Manual,” March 1, 1995. 1 (e) Public Law 116-92, “National Defense Authorization Act for Fiscal Year 2020,” December 20, 2019 (f) Intelligence Community Directive 704, “Personnel Security Standards and Procedures Governing Eligibility for Access to Sensitive Compartmented Information and Other
Cyber Awareness Challenge 2022 Online Behavior
dl.dod.cyber.milUNCLASSIFIED Online Behavior ... • If you work with classified or sensitive material as a Federal Government civilian employee, military member, or contractor: o Inform your security POC of all non-professional or non-routine contacts with foreign nationals, including, but not limited to, joining each other’s social media sites
WHO Gender Responsive Assessment Scale: criteria for ...
www.who.intLevel 3: Gender-sensitive † Considers gender norms, roles and relations † Does not address inequality generated by unequal norms, roles or relations † Indicates gender awareness, although often no remedial action is developed Level 4: Gender-specific † Considers gender norms, roles and relations for women and men and how they affect ...
Working with Official information - GOV.UK
assets.publishing.service.gov.ukhighly sensitive information relating to defence, diplomacy or national security. 01 It is your responsibility to: ensure that all information that has been entrusted to you receives the appropriate degree of care and protection. It is your organisation’s responsibility to:
ANNUAL SECURITY REFRESHER TRAINING - Northrop …
www.northropgrumman.comUnclassified government material is material that does not require a security clearance. However, it can still be very sensitive information and require special handling. Examples of t his type of data are For Official Use Only (FOUO) and Controlled Unclassified Information (CUI). These types of information are not for public disclosure.
Briefing for providers: Nursing Associates
www.cqc.org.ukIntroduction The new role of nursing associate is being introduced in health and social care services in England. The Nursing and Midwifery Council (NMC) published ... ensuring that nurse-sensitive quality indicators are taken into account to …
Meticillin Resistant Staphylococcus Aureus MRSA Protocol 1
www.kch.nhs.ukMeticillin resistant strains of Staphylococcus aureus are known as MRSA. Although MRSA is much less common than the normal meticillin sensitive strains of S aureus (MSSA), they are more likely to be found in healthcare settings.MRSA is resistant to all beta lactam
DEPARTMENT OF DEFENSE CONTROL SYSTEMS SECURITY ...
dl.dod.cyber.milSensitive Compartmented Information (SCI) classification must follow existing DoD and Intelligence Community (IC) policies, as applicable. ... (SCADA), industrial and process controls systems, cyberphysical systems, facilities-related - control systems and other types of industrial measurement and control systems . Control systems
Building Cultural Competence - Advocates for Youth
www.advocatesforyouth.orgoccur. Being culturally competent is “more than being sensitive to ethnic differences, more than not being a bigot and more than the warm, fuzzy feeling of feeling of loving and caring for your neighbor.”3 Gaining cultural competence is a long-term, developmental process.
QUICK START GUIDE FOR INDUSTRY
www.dcsa.milSafeguarding Controlled Unclassified Information (CUI) is a Department of Defense (DOD) requirement and a key tool for the protection of sensitive, unclassified information. This guide provides basic facts for industry, answers frequently asked questions, and provides sources of more detailed information and tools. CONTENTS. 3 CUI Overview
DD Form 254, Department of Defense Contract Security ...
www.secnav.navy.mila. communications security (comsec) information b. restricted data c. critical nuclear weapon design information d. formerly restricted data e. intelligence information (1) sensitive compartmented information (sci) (2) non-sci f. special access information g. nato information h. foreign government information i. limited dissemination information j.
ESD9X3.3ST5G - ESD Protection Diode - ON Semiconductor
www.onsemi.comFor sensitive circuit elements it is important to limit the voltage that an IC will be exposed to during an ESD event to as low a voltage as possible. The ESD clamping voltage is the voltage drop across the ESD protection diode during an ESD event per the IEC61000−4−2 waveform. Since the IEC61000−4−2 was written as a pass/fail spec for ...
Indicators of health - Government Medical College and ...
gmch.gov.inIndicators of Health • To measure the health status of a community • To compare the health status of country with that of another. • Characteristics of indicators: Should be valid Should be reliable & objective Should be sensitive Should be specific Should be …
Similar queries
Sensitive, Latency Sensitive Workloads, VMware, Latency-sensitive workloads, Implementing Rules and Regulations of, OF SENSITIVE CONVENTIONAL, Arms, Security, Physical, EnPress, EnPress® pressure sensitive adhesive, Adhesive, Meticillin- Sensitive, Meticillin-sensitive Staphylococcus aureus, Privacy, Nutrition Targets and Indicators for, Quality, Latency, Sensitive Compartmented Information (SCI) Administrative Security, Sensitive compartmented information, Security information, NUTRITION, Nurse, Sensitive quality indicators, People with, Physical security, Sensitive conventional arms, Market, Handling confidential information, Highly, GLUTEN SENSITIVE DINNER MENU, Tower, Maine, Intrusion Detection, Technical, Great, Streets, Context, Archives, Safeguards, Unclassified, Indicators, Sensitive indicators, Quality Indicators Sensitive to Nurse Staffing, GUIDELINES FOR MANAGEMENT OF SANITARY WASTE, Guidelines, Water, Information Security, PRESCRIBING INFORMATION, SOMATOM Force, Force, Privacy policy, DATA PRIVACY POLICY, Department of Defense MANUAL, Compartmented Information, WHO Gender Responsive Assessment Scale, Gender-sensitive, Gender, Highly sensitive, Northrop, Sensitive information, Unclassified Information, Information, Nursing, Introduction, Meticillin, Meticillin sensitive, Facilities, Culturally