Cryptographic hash functions from expander graphs
Cryptographic hash functions from expander graphs Denis X. Charles 1, Eyal Z. Goren2, and Kristin E. Lauter ... We are concerned in this paper with unkeyed hash functions which are collision resistant. Unkeyed hash functions do not require a secret key to ... bits. We propose to use a graph of
Tags:
Form, Paper, Functions, Bits, Graph, Expanders, Cryptographic, Hash, Cryptographic hash functions from expander
Information
Domain:
Source:
Link to this page:
Please notify us if you found a problem with this document:
Documents from same domain
A survey of attacks on Ethereum smart contracts
eprint.iacr.orgA survey of attacks on Ethereum smart contracts Nicola Atzei, Massimo Bartoletti, and Tiziana Cimoli ... The success of Bitcoin, a decentralised cryptographic currency that reached a ... contracts secure. Indeed, several security vulnerabilities in Ethereum …
Contract, Smart, Secure, Attacks, Decentralised, Ethereum, Attacks on ethereum smart contracts
LPN Decoded - Cryptology ePrint Archive
eprint.iacr.orgLPN Decoded Andre Esser, Robert Kubler, and Alexander May Horst G ortz Institute for IT Security Ruhr University Bochum, Germany Faculty of Mathematics
Homomorphic Encryption for Arithmetic of Approximate …
eprint.iacr.orgKeywords. Homomorphic encryption, approximate arithmetic 1 Introduction Homomorphic encryption (HE) is a cryptographic scheme that enables homomorphic oper-ations on encrypted data without decryption. Many of HE schemes (e.g. [18, 6, 7, 4, 5, 25, 33, 2, 26, 13, 12, 21, 19]) have been suggested following Gentry’s blueprint [23]. HE can be
Lattice Based Cryptography for Beginners
eprint.iacr.orgII Introduction to Ring-LWE 27 ... 14.6 Computing the Hermite Normal Form of hgiby computing the Hermite Normal Forms of h(1+ag)K 2b(1) and h(1+ag)K 2b(1)g ... that is, parallel translation by lattice vectors of parallelepiped covers Rnwithout overlap. Proof. For …
Revive: Rebalancing Off-Blockchain Payment Networks
eprint.iacr.orgRevive: Rebalancing O˙-Blockchain Payment Networks Rami Khalil Department of Computer Science ETH Zurich, Switzerland [email protected] Arthur Gervais
Network, Payments, Blockchain, Revive, Blockchain payment networks
Intel SGX Explained
eprint.iacr.orgcomputer, and a message produced by the container. improvements for enclave authors, it is a small incre-mental improvement, from a design and implementation standpoint. After understanding the principles behind SGX 1 and its security properties, the reader should be well equipped to face Intel’s reference documentation
Somewhat Practical Fully Homomorphic Encryption
eprint.iacr.orgf(x) 2Z[x] is a monic irreducible polynomial of degree d. In practice one would typically restrict to using a cyclotomic polynomial m(x), i.e. the minimal polynomial of the primitive m-th roots of unity. The most popular choice for expository purposes is to take f(x) = xd+ 1 with d= 2n. Elements of the ring Rwill be denoted in lowercase bold, e ...
Practical Secure Aggregation for Privacy-Preserving ...
eprint.iacr.orgwithdistinctfieldelementsinF.Giventheseparameters,the scheme consists of two algorithms. The sharing algorithm SS.share(s,t,U) →{(u,s u)} u∈U takes as input a secret s, a set Uof nfield elements representing user IDs, and
How To Simulate It – A Tutorial on the Simulation Proof ...
eprint.iacr.orgOrganization. In this tutorial, we will demonstrate the simulation paradigm in a number of different settings, together with explanations about what is required from the simulator and proof. We demonstrate the aforementioned three different tasks of the simulator in simulation-based proofs via a gradual progression.
Universally Composable Security: A New Paradigm for ...
eprint.iacr.orgWe call this composition operation universal composition and say that de nitions of security in this framework (and the protocols that satisfy them) are uni-versally composable (UC). Consequently, we dub this framework the UC security framework.1 As we shall see, the fact that security in this framework is preserved under universal composition ...
Security, Universal, A new, Universally, Universally composable security, Composable
Related documents
Contents Introduction - University of Chicago
math.uchicago.eduIn this paper we present a graph property with sensitivity (p n), where n = v 2 is the number of variables, and generalize it to a k-uniform hy-pergraph property with sensitivity (p ... bits in any single block ips the value of f(x). We present these de nitions with precise mathematical notation in section 2. It is clear from the de nition that for
Lab #1 - MATH
math.slu.edu• Graph paper • Calculator Software: • C compiler (or other high-level programming language) INTRODUCTION Computers store information as "bits", short for binary digit. A bit is a 0 or a 1, but can be represented in many ways. For example, as "true" or "false", or a light being on or off. In a
Paper, Math, Bits, Graph, Graph paper
Graphs, Charts, and Tables Lesson Plan - KET
tdcms.ket.orgGraphs, Charts, and Tables Lesson Plan Video Set up the video by reminding students that data is information and information is ... • Data are bits of information that can be organized in tables. ... • Graphs, charts, and tables are not only found on the Math test, but also on the Social Stud-ies and Science tests. • Read titles carefully ...
Chart, Plan, Table, Lesson, Math, Bits, Graph, And tables lesson plan
Matrix Transformations Name Lab Activity In the movie ...
mrsroberts.comMatrix Transformations Name_____ Lab Activity In the movie, Matrix Revolutions, ... Using graph paper, show the locations of the original Agent Smith and all of his replicas. ... graph Neo and graph Neo’s dilation D3. Show your LIST values. Show formulas used to create L3-L4. Di splay Neo and his enlargement below. L1 L2 L3 L4
Name, Activity, Paper, Transformation, Matrix, Graph, Graph paper, Matrix transformations name lab activity in
Rotation; Geometry; 7
www.doe.virginia.govReturn the patty paper, the x-axis and y-axis, and the trapezoid to their original positions on the graph. Rotate the entire piece of patty paper 180° counterclockwise about the origin.
MathBits
www.freetemplatedownloads.netMathBits.com . Created Date: 8/25/2016 6:39:53 PM
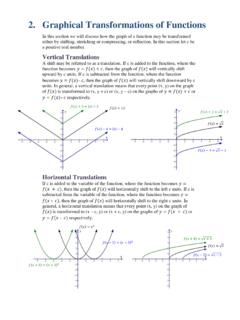
2. Graphical Transformations of Functions
michelenaja.faculty.mjc.edu2. Graphical Transformations of Functions In this section we will discuss how the graph of a function may be transformed either by shifting, stretching or compressing, or reflection.
Transformation, Functions, Graph, Graphical, Graphical transformations of functions
Graph Theory, Part 2 - Home | Math
web.math.princeton.eduGraph Theory, Part 2 7 Coloring Suppose that you are responsible for scheduling times for lectures in a university. You want to make sure that any two lectures with a …
30x40 - Math Help - Math Skills - Math Practice
www.emathlab.com30x40. Title: 36x48 Author: John Schlecht Created Date: 8/2/2005 10:58:29 PM ...
ALGEBRA 2/TRIGONOMETRY - Regents Examinations
nysedregents.org34 On the Algebra 2/Trigonometry midterm at Champion High School, the scores of 210 students were normally distributed with a mean of 82 and a standard deviation of 4.2. Determine how many students scored between 79.9 and 88.3.
Examination, Regent, Regents examinations, Algebra, Trigonometry, Algebra 2 trigonometry
Related search queries
Paper, Graph, Bits, Lab #1, Math, Graph paper, Graphs, Charts, and Tables Lesson Plan, Matrix Transformations Name Lab Activity In, Matrix Transformations Name_____ Lab Activity In, Rotation, Geometry, 2. Graphical Transformations of Functions, Graph Theory, Part 2, 30x40, Algebra 2/Trigonometry, Regents Examinations