Transcription of DEPARTMENT OF INFORMATION TECHNOLOGY
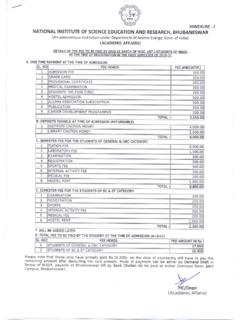
1 Full Time INFORMATION SECURITY & CYBER FORENSICS CURRICULUM & SYLLABUS 2013 -2014 DEPARTMENT OF INFORMATION TECHNOLOGY FACULTY OF ENGINEERING AND TECHNOLOGY SRM UNIVERSITY SRM NAGAR, KATTANKULATHUR 603 203 1 DEPARTMENT OF INFORMATION TECHNOLOGY FULL TIME INFORMATION SECURITY AND CYBER FORENSICS CURRICULUM & SYLLABUS 2013 -2014 Course code Course Name L T P C I AND II SEMESTER IS2001 Introduction to Cryptography 3 0 2 4 IT2001 Data Structures and Algorithms 3 0 2 4 IS2002 Operating Systems.
2 Administration and Security 3 0 2 4 IS2003 Network Security 3 0 2 4 IS2004 TCP/IP 3 0 2 4 IS2005 Forensics and Incident Response 3 0 2 4 III SEMESTER IS2047 Seminar 0 0 1 1 IS2049 Project Work Phase-I 0 0 12 6 IV SEMESTER IS2050 Project Work Phase-II 0 0 32 16 SUPPORTIVE COURSE MA2019 Number Theory 3 0 0 3 INTER DISCIPLINARY ELECTIVE One course to be taken in Semester I or II or III 3 0 0 3 PROGRAM ELECTIVES 6 courses of 3 credits each to be taken in Semesters I -III - - - 18 TOTAL CREDITS 71 Total Number of credits to be earned for degree: 71 CONTACT HOUR/CREDIT: L: Lecture Hours per week T: Tutorial Hours per week P: Practical Hours per week C: Credit 2 PROGRAM ELECTIVES Course code Course Name L T P C IS2101 Applied Cryptography 3 0 0 3 IS2102 Principles of Secure Coding 2 0 2 3 IS2103 Mobile and Digital Forensics 3 0 0 3 IS2104 Mobile and Wireless Security 3 0 0 3 IS2105 Interactive Programming with Python 2 0 2 3 IS2106 Malware Analysis 2 0 2 3 IS2107 Penetration Testing and Vulnerability Assessment.
3 2 0 2 3 IS2108 Computer and INFORMATION Security Management 3 0 0 3 IS2109 Risk Assessment and Security Audit 3 0 0 3 IS2110 Storage Management and Security 3 0 0 3 IS2111 Cloud Architectures and Security 2 0 2 3 IS2112 Cyber Law 3 0 0 3 NOTE: Students have to register for the courses as per the following guidelines: Sl. No. Category Credits I Semester II Semester III Semester IV Semester Category Total 1 Core courses 12 ( 3 courses) 12 ( 3 courses) --- --- 24 2 Program Elective courses 18 (in I to III semesters) --- 18 Interdisciplinary elective courses (any one program elective from other programs) 3 (One course to be taken in Semester I or II or III) 3 3 Supportive courses - mandatory 3 (One course to be taken in Semester I or II or III)
4 --- 3 4 Seminar --- --- 1 --- 1 6 Project work --- --- 06 16 22 Total 71 3 I AND II SEMESTER IS2001 INTRODUCTION TO CRYPTOLOGY L T P C Total Contact Hours 75 3 0 2 4 Prerequisite Nil PURPOSE The course provides a comprehensive view of symmetric and asymmetric cryptographic Schemes and key management issues. INSTRUCTIONAL OBJECTIVES 1. Understand OSI security architecture and classic encryption techniques 2. Acquire fundamental knowledge on the concepts of finite fields and number theory 3. Understand various block cipher and stream cipher models 4.
5 Describe the principles of public key cryptosystems, hash functions and digital signature UNIT 1- INTRODUCTION (9 hours) Services, Mechanisms and attacks-the OSI security architecture-Network security model classical Encryption techniques (Symmetric cipher model, substitution techniques, transposition Techniques, steganography). UNIT II- FINITE FIELDS AND NUMBER THEORY (9 hours) Groups, Rings, Fields-Modular arithmetic-Euclid s algorithm-Finite fields-Polynomial. Arithmetic Prime numbers-Fermat s and Euler s theorem-Testing for primality -The theorem- Discrete UNIT III- BLOCK CIPHERS (9 hours) Data Encryption Standard-Block cipher principles-block cipher modes of Standard (AES)-Triple DES-Blowfish-RC5 algorithm.
6 UNIT IV- PUBLIC KEY CRYPTOGRAPHY (9 hours) Principles of public key cryptosystems-The RSA algorithm-Key management -Diffie exchange-Elliptic curve arithmetic-Elliptic curve cryptography. 4 UNIT - V HASH FUNCTIONS AND DIGITAL SIGNATURES (9 hours) Authentication functions-Message authentication codes-Hash functions-Hash Algorithms (MD5, Secure Hash Algorithm)-Digital signatures (Authentication protocols, Digital signature Standard ). PRACTICAL: (30 hours) REFERENCE BOOKS: 1. William Stallings, Cryptography and Network Security , Pearson Education, 6th Edition, SBN 10: 0133354695, 2013.
7 2. AtulKahate, Cryptography and Network Security , McGraw Hill Education India (Pvt Ltd),2nd edition, ISBN 10: 0070151458, 2009. 3. Charlie Kaufman, Radia Perlman, Mike Speciner, Network Security: Private Communication in a Public World , Prentice Hall, 2 nd edition, ISBN 10: 0130460192, 2002. 4. Charles Pfleeger, Shari Lawrence Pfleeger Security in computing , Prentice Hall,4th Edition, ISBN 10: 0132390779, 2006. IT2001 DATA STRUCTURES AND ALGORITHMS L T P C Total Contact Hours - 75 3 0 2 4 Prerequisite NIL PURPOSE: Data structures play a central role in modern computer science.
8 You interact with data structures much more often than with algorithms (think of Google, your mail server, and even your network routers). In addition, data structures are essential building blocks in obtaining efficient algorithms. This course will cover major results and current directions of research in data structures. INSTRUCTIONAL OBJECTIVES 1. To make the student learn a object oriented way of solving problems. 2. To make the student write ADTS for all data structures. 3. To make the student learn different algorithm design techniques.
9 UNIT I - OVERVIEW OF C++ (5 hours) C++ class overview-class definition-objects-class members- access control- constructors and destructors-parameter passing methods-dynamic memory allocation and de-allocation-Function overloading. 5 UNIT II - LINEAR DATA STRUCTURES AND ALGORITHM ANALYSIS (7 hours) Review of Arrays-Stacks-Queues-linked lists-Linked stacks and Linked queues-Applications- Efficiency of algorithms-Asymptotic Notations- Time complexity of an algorithm using O notation- Average- Best- and Worst Case Complexities- Analyzing Recursive Programs.
10 UNIT III - NON LINEAR DATA STRUCTURES AND HASH TABLES (14 hours) Introduction- Definition and Basic terminologies of trees and binary trees- Representation of trees and Binary trees- Binary tree Traversals- Threaded binary trees- Graphs- basic concepts - representation and traversals. Introduction- Binary Search Trees: Definition- Operations and applications. AVL Trees: Definition- Operations and applications. B Trees: Definition- Operations and applications. Red Black Trees- Splay Trees and its applications.