Transcription of Risk Register - University of Sheffield
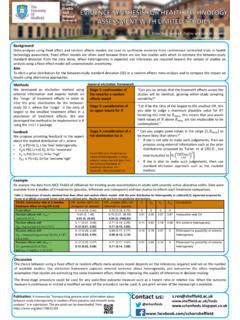
1 Corporate Information and Computing Services Risk Register February 2016 CiCS manages the risks to the ICT infrastructure that supports most of the vital functions of the University . Our internal risk management information will have a more complex structure than the Register layout suggested. Each system or service supports various types of vital activity in the University and is at risk from many causes, each with its own preventive measures. Systems are also heavily interdependent. The recommended Risk Register layout has too few dimensions to express this complexity and can only provide a simple summary. Loss or degradation of any ITC system would clearly be categorised as an infrastructure risk, but this could be misleading as learning, financial processes, research etc could all be affected equally.
2 Instead we have given more than one category, as a number, against most risks . To give them in order of risk exposure would be almost meaningless and this has not been attempted. We have not listed planned actions against most risks . Many major actions were identified earlier and are now complete. They are shown as controls in the Register . These are either major investments in equipment and facilities, or ongoing processes within CiCS. Further actions are likely to be identified as the new assessment process develops. CiCS has a Business Continuity Plan and a great deal of other information to be used when various types of incidents occur. This has not been mentioned in the Register as it applies to every risk. We have not listed opportunities alongside the risks .
3 They are a very different type of issue in this area. Categories Most CiCS items relate to 1, 4, 6 and 7 , Infrastructure, IT, Business Continuity relationships and partners , Teaching, Student experience development and strategy and innovation quality and Human Resources Category Description Inherent Controls in place Residual Further Actions Due date and person Other L I L I risks related to resourcing 1, 4, 6, 7 Under funding and obsolescence of IT resources. Lack of investment leads to reliability and security issues, plus accumulation of long term maintenance backlog which reduces flexibility, reduces product quality, increases upgrade times and generates unpredictability. Departments may then take things into their own hands, creating a chaotic set of facilities.
4 L M Constant attention to changing needs and funding issues, including continuation of capital budget. Prioritise spending and effort clearly. Current funding issues affect this risk. M M . 1,7 Loss of key personnel. Many systems are understood by only one person, who could leave, become ill, have an accident etc. Some systems could then be difficult to maintain, with extended down time, or projects could be delayed. M M Identify key personnel Share expertise and train others in key skills. Document key systems carefully. Maintain staff retention through health and morale in the workplace, deal with grievances properly. Standardise systems and processes to reduce reliance on individuals. Outsource specialist skills to competent third parties. Use SRDS etc effectively.
5 M L risks involving loss of use of software 1 Major supplier goes out of business or taken over by a rival. Leads to inability to maintain specific items, unreliability or high cost of replacing everything supplied . M H Use purchasing agreements that include alternate suppliers. Use of major suppliers more likely to be taken over if they fail. Awareness of alternative approaches. Avoid obvious dependencies. M M 1, 4 Software licensing changes. Software supplier could withdraw licenses for vital items, significantly change the price, go out of business, sell rights etc. Affects costs and ability to provide items widely. Risk prosecution if unaware. M M Awareness of forthcoming changes and alternatives. Membership of consortia. Negotiate good deals.
6 Check contracts. Good relations with suppliers. Pay annual costs when due. L M 1,4,6,7, Failure of applications software, eg triggered by incompatibility due to changes in related systems or by increased demands. This could lead to unavailability of particular services and possible extra costs. M M Keep software maintenance contracts up to date. Application of patches and implementation of new versions as they are provided for central systems. Commitment to maintenance windows so software & hardware for key business systems can be kept supportable Appropriate testing of software and its effective and robust configuration, M L version and change management. Good documentation of procedures and dependencies. Risk arising from external constraints 1 Changes to systems required by legislation, or new requirements from funding bodies Possible requirement to stop using existing processes if not planned ahead.
7 M M Constant attention to and understanding of legislation and good liaison with funding bodies. Information Security Officer in place. PCI/DSS compliance being addressed. M L 1, 2 Outsourced services (including Google Apps for Education, Blackboard Learn, Talis, Planon, and StarRez) Potential for loss of services and service quality, reputation and security risks , legal issues (data protection, export laws). M M Careful checking of third party services and systems Use only major players. Correct contractual agreements. Effective Supplier Relationship Management. Constant monitoring and robust exit plans in place. L L risks related to internal communication and understanding of needs 7 Unrealistic expectations of CiCS services. Failure to manage expectations and understanding of services could lead to bad feeling, complaints, unrealistic demands and pressure lowering service quality.
8 M M Range of communication channels to inform users of services and changes. Customer Services and Communication team established Liaison channels established and continue to L L develop, especially at faculty level. Develop effective mechanisms for prioritisation involving all relevant stakeholders. 7,6,1 Failure to provide services that are needed. If CiCS does not provide IT services that departments need (or want) they will find their own solutions. This would lead to duplication of effort, extra overall cost, poorer quality and reliability and reduced cooperation. M M As for Unrealistic expectations above. Working in an agile way to more quickly provide solutions Introducing a business partnership model for better understanding Faculty IT requirements L L risks arising from malicious activity 1,7 Internal fraud or sabotage.
9 Disgruntled (or simply untrained) staff could do enormous damage to IT systems and data or bring the University into disrepute L VH Attention to health and morale of staff. Charter for system Administrators is regularly issued to all relevant staff. Access rights are allocated carefully for key systems. Training on security procedures. Information Security Manager in place. L M Information Security awareness raising programme across the University includes guidance on security and statement of personal responsibilities. 1,4,6,7, Unauthorised access to computers and data. H M A Code of Conduct for all computer users, including M L Information Security awareness raising programme across the May be malicious, hacking etc. Could lead to serious breach of University security or create a route to hack other sites.
10 Security advice, is published and promoted. Appropriate detection systems in place. Monitor attempts to gain unauthorised access. Allocated rights carefully for sensitive systems. Manage expired accounts properly. University includes guidance on security and statement of personal responsibilities. 1, 4, 6, 7 Virus or other malware attack, or software vulnerabilities. Malicious software can damage any IT system, or prevent normal service by sheer volume of extra traffic. The problem could spread through many computers including to other sites and take days to clear. Denial of Service Attacks to University or outsourced systems. VH VH Use high quality virus/malware detection systems at the centre and encourage or enforce use on all users computers.