Search results with tag "Configuration"
OPC UA Configuration Manager - Kepware
www.kepware.comOPC UA Configuration Manager The OPC UA Configuration Manager assists users in administering the UA server configuration settings. OPC UA's security requires that all endpoints participating in UA communication do so over a secure con-nection. To comply with this security requirement, each UA server instance and UA client instance must
May 2019 iSC250 Installation and Configuration Guide
www.elavonpayments.comL5300 Installation and Configuration Guide. to enter the [0] [1] [2] [1] Ingenico ISC250 USB Mode Configuration Steps [-] 2 [+] TDA. keypad to save all configuration ...
UDS1100 User Guide - Lantronix
www.lantronix.com4: Using DeviceInstaller Instructions for viewing the current configuration using DeviceInstaller. 5: Configuration Using Web-Manager Details using the Web-Manager to set parameters such as port and server properties. 6: Configuration via Telnet or Serial Port (Setup Mode Provides instructions for accessing Setup Mode (command line
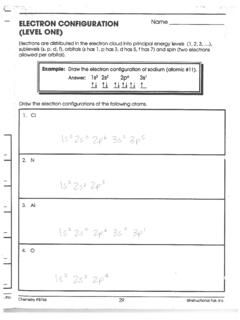
Electron Configuration Practice Worksheet
www.mayfieldschools.orgElectron Configurations - Solutions Note: The electron configurations in this worksheet assume that lanthanum (La) is the first element in the 4f block and that actinium (Ac) is the first element in the 5f block. If your periodic table doesn’t agree with this, your answers for elements near the f-orbitals may be slightly different.
Cisco IR910 Software Configuration Guide, Release 1.0 - Cisco
www.cisco.comCisco 910 Industrial Router Software Configuration Guide, Release 1.0 OL-31296-01 8 Configuring VLANs This chapter describes how to configure VLANs on the Cisco 910 Industrial Routers (hereafter referred to as the router). It includes information about VLAN membership modes, VLAN configuration modes, and VLAN trunks.
Cisco 220 Series Smart Switches Administration Guide
www.cisco.comDownload/Backup Configuration or Logs 49 Configuration File Properties 51 ... Chapter 15: IP Configuration 179 IP Addressing 179 IPv4 Management and Interface 181 ... computer with Internet Explorer 8.0 (or higher), Firefox 20.0 (or higher), Chrome
Using the Software Upgrade Tool in the Web Configuration ...
support.polycom.comcheck for new software versions and quickly upgrade phones on an individual basis. These tools are available for all phones using Polycom® UC Software 4.0.0 or later. The Software Upgrade options (shown next) built into the Web Configuration Utility provide you with a convenient way to upgrade (or downgrade) software for small phone deployments.
ProSafe Plus 8-port Gigabit Switch with 4-Port PoE …
www.downloads.netgear.comThe switch configuration utility is installed in the program directory of your computer and a ProSafe Plus Utility icon is placed on your desktop. Configure the switch: 1. Double-click the ProSafe Plus Utility icon. The configuration home screen displays a list of plus switches that it discovers on the local network. 2.
Switch Configuration Example for Q ... - QSC Audio Products
www.qsc.comThis switch configuration example is intended to serve as a network setup guideline for systems using Q-LAN audio and video streaming within your Q-SYS system and should be used alongside the Q-SYS Networking requirements in Q-SYS Help for deeper setup insight.
Hierarchal Testbench Configuration Using uvm config db
www.synopsys.comHierarchal Testbench Configuration Using uvm_config_db 2 Figure 1: set() and get() function syntax “cntxt” and “inst_name” are used to specify the storage location or address of the object handle. When used properly these parameters define the hierarchical path to the object data. “field_name” is the name for the object.
Catalyst 3560-C and 2960-C Getting Started Guide (English)
www.cisco.comFor additional installation and configuration information for the switch, see the ... In the Switch Password field, enter your password. The password can be from 1 to 25 ... Use the device manager to perform basic switch configuration and monitoring. See the device manager online help for more information. 4.
EMC Data Domain Operating System Initial Configuration …
www.vmarena.comThis guide explains how to perform the post-installation initial configuration of an EMC Data Domain system. This preface includes descriptions of related documentation, conventions, audience, and contact information. Audience This guide is intended for use by system administrators who are responsible for
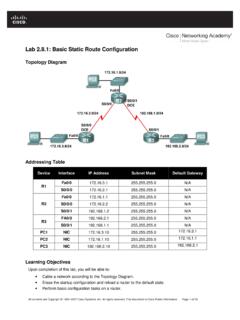
Lab 2.8.1: Basic Static Route Configuration
www2.victoriacollege.eduRouting Protocols and Concepts: Static Routing Lab 2.8.1: Basic Static Route Configuration ... static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP ...
WiFi Camera (V380) Installation Manual iPhone IOS Android
images-na.ssl-images-amazon.comInstallation Manual ... Click on “AP Quick Setup” will bring you to the Quick Configuration screen. 7. You will see the camera access point name under Quick Configuration. Click on the name to connect to the camera. 8. You should see a list of nearby WiFi networks. Choose your
KMBT 654-20131118121126 - Berger's Chemistry Class
bergerchem.weebly.comElectron Configurations Solutions Note: The electron configurations in this worksheet assume that lanthanum (La) is the first element in the 4f block and …
Electron Configurations Worksheet - Glendale Community …
web.gccaz.eduElectron Configurations Worksheet For atoms, the number of electrons = number of protons because atoms are neutral. Remember you are filling in ALL the electrons, not just valence, but ALL. The order of filling in electrons in the subshells is 1s 2s 2p 3s 3p 4s s subshells have only 1 orbital, 2 electrons per orbital = 2 electrons max
Logix 3800 Digital Positioner FCD LGENIM0112-06 01/20 …
www.slatercontrols.comLogix™ 3800 Digital Positioner FCD LGENIM0112-06 01/20 flowserve.com 6 Figure 3: Logix 3820 (HART) Internal Positioner Features Menu Control Buttons (3x) Discrete Output (2) Analog Input Analog Output 4 – Discrete Input20 mA Command Remote Mount Discrete Output (1) Configuration DIP Switches (8x) LED Indicators (5x) LCD Display Gain Switch
WirelessHART Field Device Installation and Configuration
www.emerson.comdetermined by the update rate of the wireless field device, network routing for other wireless field devices, and efficiencies of the sensor and electronics. Reference 3, the Power Module Life Estimator, provides information regarding power module life. Devices with energy harvesting or line power can operate indefinitely at very fast update rates.
Electron Configurations PowerPoint
www.birdvilleschools.netElectron Orbitals • Orbitals are clouds of probability within an energy level, so an actual orbital is a region of space, where an electron might be found. • Two orbital clouds are pictured below. There are more dots near the center of the picture, because an electron is most likely to be near the nucleus (center) of the atom (the electron
HP mt31 Mobile Thin Client 製品仕様
jp.ext.hp.comセキュリティ機能 TPM(2.0)セキュリティチップ搭載、HP BIOSphere Gen4、ユーザー別起動時パスワード(PBA)サポート、 ... マネジメント機能 HP Device Manager、HP ThinUpdate、HP BIOS Config Utility (BCU)、Microsoft System Center Configuration Manager ポインティングデバイス タッチ ...
Job Aid: Conducting Airborne Electronic Hardware Reviews
www.faa.govhardware developer, the applicant’s hardware Process Assurance (PA) and hardware Configuration Management (CM) personnel, systems engineer, and other team members should be present at on-site reviews. Hardware Developer • Includes applicant and/or developer of the hardware to be installed on an aircraft. (May be supplier to applicant.)
Dell EqualLogic Configuration Guide
i.dell.comDec 04, 2012 · designing and/or administering a shared storage solution. Also, there are some assumptions made in terms of familiarity with all current Ethernet standards as defined by the Institute of Electrical and Electronic Engineers (IEEE) as well as all TCP/IP and iSCSI standards as defined by the Internet Engineering Task Force (IETF).
MOTOTRBO™ SLR 5000 Series Repeater - Motorola
www.motorolasolutions.comachievable for the specific system configurat ion, the configuration should be modified in order to make it possible. The R56 Standards and Guidelines for Communications Sites manual provides examples of signage that can be used to identify the occupational or general public compliance boundaries.
SSL VPN Configuration Guide, Cisco IOS Release 12
www.cisco.comStateless High Availability with Hot Standby Router Protocol 23 TCP Port Forwarding and Thin Client 24 URL Obfuscation 26 URL Rewrite Splitter 27 User-Level Bookmarking 27 Virtual Templates 27 License String Support for the 7900 VPN Client 27 SSLVPN DVTI Support 27 Prerequisites for SSLVPN DVTI Support 28 Restrictions for SSLVPN DVTI Support 28
HP Z800 Memory Configuration and Optimization
h20331.www2.hp.comthe system will run at 800MHz. The CPUs determine the speed at which the memory is clocked. Example: if a 1067MHz capable CPU is included in the system, the maximum speed the memory will run at is 1067MHz regardless of the specified speed of the memory Best Performance Optimization Tips
ProSAFE Plus Configuration Utility - Netgear
www.downloads.netgear.comsystem (OS) and that is on the same network as the switches that you want to manage. If an earlier version of the utility is present on your computer, installing a newer version replaces the older version. Newer versions of the utility are backward compatible and support all previously released ProSAFE Web Managed (Plus) Series Switches.
Cours/TP n° 1 Installation et configuration d’un serveur web
users.polytech.unice.fr[2015][LPSIL][IDSE][TP1 ]nom1_Prenom1 – nom2_Prenom2 où nom1_Prenom1 et nom2_Prenom2 les noms et prénoms du binôme. • Etre reçu par votre enseignant le jour du cours/TP. • Contenir dans le corps de l’email les questions que vous pourriez avoir (si vous souhaitez avoir une
Sophos Firewall CLI Guide v17
docs.sophos.comSophos XG Firewall adheres to Cisco terminology for routing configuration and provides Cisco-compliant CLI to configure static routes and dynamic routing protocols. Traditionally, IP packets are transmitted in one of either two ways –Unicast (1 sender –1 receiver) or Broadcast (1 sender –everybody on the network).
NIST Cybersecurity Framework Policy Template Guide
www.cisecurity.orgguide to participants of the Nationwide Cybersecurity Review (NCSR) and MS-ISAC members, as a resource to assist with the application and advancement of ... Security Assessment and Authorization Policy ... Configuration Management Policy Identification and Authentication Policy Sanitization Secure Disposal Standard
The 16 and 18 Electron Rule in Organometallic Chemistry ...
www.yorku.cacalled the 16 and 18 Electron Rule. Careful subsequent study has almostinvari- ably shown that the original formulation was incorrect. The accessibility of 16 and 18 electron configurations also has important consequences for mechanisms of organometallic reactions, as outlined below.
Microsoft Azure IoT Reference Architecture Version 2.1 9 ...
download.microsoft.comcommon configuration environments, and composition of Azure IoT services, physical devices, and Intelligent Edge Devices. The primary targets of this document are architects, system designers, developers, and other IoT technical ... technology best practices. ... Storage can be divided into warm path (data that is required to be available for ...
Mobile App User Guide - iPhone - Concur Training
www.concurtraining.comThe Concur Mobile Registration link appears on the Profile menu in the web version of SAP ... depending on your company's configuration, you can use the same login credentials that you use for the web version of SAP Concur or you can use Single Sign On (known as SSO). (If your company uses SSO, this page will be slightly different.)
SOFTWARE UPGRADE 17.2 PRICE BOOK - Snap-on
www1.snapon.comSOFTWARE UPGRADE 17.2 HIGHLIGHTS WHAT’S NEW FOR EDGE SERIES OWNERS. 4 5 Vehicle Software Coverage and Smart Vehicle Interface P/N EAK0347L01A ... Reprogram Key FOBs, Alarm, Side Car Configuration, Dash Lights and LCD Segments, Speedometer, Tachometer. Customers Who Are Interested in This Coverage • Harley-Davidson specialty …
IQ Range full configuration, status and monitoring user …
www.rotork.comClear: Rotork Bluetooth® Setting Tool Pro Connecting to the actuator using Bluetooth The actuator must be powered up to connect using Bluetooth. The default security set in the actuator for Bluetooth connection is by initiation using an infrared command. This means that the user must be in close proximity and in direct line of sight of the ...
control plane policing copp - Cisco
www.cisco.comCHAPTER 75-1 Cisco IOS Software Configuration Guide, Release 15.0SY 75 Control Plane Policing (CoPP) • Prerequisites for CoPP, page 75-1 † Restrictions for CoPP, page 75-2 † Information About CoPP, page 75-3 † Default Settings for CoPP, page 75-3 † How to Configure CoPP, page 75-5 † Monitoring CoPP, page 75-9 Note † For complete syntax and usage …
CounterACT Endpoint Module HPS Inspection Engine ...
www.forescout.comEndpoint Module: HPS Inspection Engine Configuration Guide Version 10.8 5 . About the HPS Inspection Engine . The HPS (Host Property Scanner) Inspection Engine is a component of the ForeScout CounterACT ® Endpoint Module. See . Endpoint Module Information. for details about the module. The HPS Inspection Engine allows CounterACT to:
Modbus configuration guide - ABB
library.e.abb.comTechnical Bulletin 180 TFIO Communication Interface Module (2100421 BD) (CIM) and Modbus Protocol Tekbul 180 Technical Bulletin 182 NGC Modbus Registers assignments in the NGC 8200 Tekbul 182 User Drawing XFC G4 Com 1 to ABB Coriolis Meter using Hart Modbus Converter 2104918 User Drawing XRC G4 Adapting K-TEK for Modbus RS-485/COM2 on a 12 …
Configuring Tunnel Groups, Group Policies, and Users - Cisco
www.cisco.comCisco ASA 5500 Series Configuration Guide using the CLI 67 Configuring Connection Profiles, Group Policies, and Users This chapter describes how to configure VPN connection profiles (formerly called “tunnel groups”), group policies, and users. This …
RT-N12 Series - Asus
dlcdnet.asus.com3 Network configuration using the web GUI 22 ... • Place the wireless router at the center of your network for maximum wireless coverage. ... • Web browser such as Microsoft Internet Explorer, Mozilla Firefox, Apple Safari, or Google Chrome NOTE:
Enterprise Security Architecture for Cyber Security
www.opengroup.org(BS 25999-2:2007). Cyber Security Source: 9 Steps to Cyber Security – The Manager’s Information Security Strategy Manual (Dejan Kosutic) Cyber Security in South Africa Source: SA-2012-cyber-threat ... configuration Examples Certification and Audit Security Measures
LOGITECH FOR MICROSOFT TEAMS ROOMS ON ANDROID
www.logitech.comTeams® Room with one-touch join, wired and wireless content sharing, and center-of-room control with Tap. Logitech® solutions for Microsoft Teams Rooms on Android™ are preconfigured for simplified setup and management. Choose small, medium, or large configurations, then customize with mounts and accessories to suit each space.
How to Work with SAP Business One Microsoft 365 Integration
help.sap.comThe configuration URL is supported in the following web browsers: Google Chrome, Microsoft Edge (based on Chromium), Mozilla Firefox, and Apple Safari. To check whether the Microsoft Edge browser is based on Chromium, choose Help and feedback About Microsoft Edge . 2.
Software and Hardware Configuration Management - NASA
www.nasa.govMay 19, 2017 · Jeffrey Northey (original signature on file) IMS Manager 05/19/2017 Jerry Sims (original signature on file) Process Owner 05/19/2017 REFERENCES Document ID/Link Title IVV QM NASA IV&V Quality Manual IVV 11 Enterprise Architecture (IT Governance) IVV 16 Control of Records NPR 1441.1 NASA Records Management Program Requirements
OPTIMISATION DE CONFIGURATION D’UN ENTREPÔT ET …
biblos.hec.caAux fils des années, des changements au sein de l’environnement concurrentiel de l’industrie du commerce de détail à Taïwan sont intervenus et se sont manifestés sous plusieurs formes.
Protecting Information and System Integrity in Industrial ...
www.nccoe.nist.govInformation and System . Integrity in Industrial Control System . Environments: ... and provide users with the materials lists, configuration files, and other information they need to implement a similar approach. ... second-most targeted industry (C. Singleton et al., X-Force Threat Intelligence Index 2021, IBM, February 2021, https://www.ibm ...
Polycom OBi302 Installation and Configuration Guide
support.polycom.comPolycom OBi302 Installation and Con˜guration Guide 1 Installation Requirements Check that you have the following: Polycom OBi302 device Ethernet cable Power adapter You also need: Touch-tone phone Active internet connection Access to the internet via an Ethernet port on your router or modem Note: You can use the OBi302 as a router by connecting the OBi302 device …
Similar queries
Configuration, Client, Installation, User Guide, Manager, Electron, Electron configurations, Cisco, Software Configuration, IPv4, Internet, Upgrade, Polycom, ProSafe Plus 8-port Gigabit Switch with 4-Port, Configuration utility, ProSafe Plus Utility, Plus, Switch Configuration Example for Q, Audio, Audio and video, Field, Device, Guide, Basic Static Route Configuration, Routing, IGRP, EIGRP, OSPF, Installation Manual, Quick, Quick Configuration, 3800 Digital Positioner FCD LGENIM0112-06, WirelessHART Field Device Installation and Configuration, Wireless, Sensor, Energy, Orbital, Utility, Hardware, And hardware Configuration Management, Dell EqualLogic Configuration Guide, Administering, Motorola, Configurat ion, SSL VPN Configuration Guide, Cisco IOS Release, Hot Standby Router Protocol, Z800 Memory Configuration and Optimization, 800MHz, ProSAFE Plus Configuration Utility, Netgear, Switches, Managed, N° 1 Installation et configuration d’un, IDSE, Security Assessment, Best practices, Storage, Profile, UPGRADE 17.2, Snap-on, Full configuration, status and monitoring user, Bluetooth, User, Module: HPS Inspection Engine Configuration Guide, Scanner, Modbus configuration guide, Technical, Group policies, and users, Configuration Guide, RT-N12, Center, Microsoft, Enterprise Security Architecture, 2007, Logitech, Room, Configurations, Software and Hardware Configuration Management, NASA, Quality, OPTIMISATION DE CONFIGURATION D’UN, Formes, System, Polycom OBi302 Installation, Polycom OBi302, OBi302