Search results with tag "Authentication"
FIPS 198-1, The Keyed-Hash Message Authentication Code …
csrc.nist.govThe Keyed-Hash Message Authentication Code (HMAC) (FIPS PUB 198-1). 2. Category of Standard. Computer Security Standard. Subcategory. Cryptography. 3. Explanation. This Standard specifies an algorithm for applications requiring message authentication. Message authentication is achieved via the construction of a message authentication code (MAC).
Table of Contents - Mastercard
www.mastercard.desingle authentication is linked to multiple authorizations, the same authentication code/AAV as per PSD2 RTS could be used for multiple transactions. 2.4. Issuer Authentication Value (IAV) The IAV is pertinent to Issuers who perform themselves the validation of the authentication code (self-validation). It is :
Administration VMware Identity Manager
docs.vmware.comConfigure RSA Adaptive Authentication in Identity Manager 56 Configuring a Certificate or Smart Card Adapter for Use with VMware Identity Manager 58 Using User Principal Name for Certificate Authentication 58 Certificate Authority Required for Authentication 59 Using Certificate Revocation Checking 59 Configure Certificate-based Authentication ...
Kentucky Online 'ateway Multi-&actor Authentication (M&A ...
kog.chfs.ky.gov1. After logging in to their KOG account, the user will click the [Launch] button to open an application that requires multi-factor authentication (in this case, Identity Proofing). 2. A Multi-Factor Authentication screen will appear in KOG that includes fields for the user to enter
Setup Guide: Server-side synchronization for CRM Online
download.microsoft.comThe authentication mechanism is Basic authentication. For that, CRM requires that you set up a service account in Exchange with an impersonation role. For more information on enabling Basic authentication, see: Exchange Server 2010: Configure Exchange Server 2010 Impersonation Exchange Server 2013: Impersonation and EWS in Exchange
BANKING AUTHENTICATION METHODS - InfoSecWriters.com
www.infosecwriters.com(Wikipedia, 2005) In other words, someone has the need to verify that someone else is who they say they are. Authentication can be completed via the use of many different methods. Some of these methods are far superior to others, but are more difficult to implement and fund. Authentication is not enough to grant users access on its own.
Completing the COVID-19 Daily Symptom Questionnaire If …
hmhmaestro.orgbypassing the step of choosing an authentication method each login. ... CHOOSE AN AUTHENTICATION METHOD AND COMPLETE ENROLLMENT You have successfully enrolled in Duo’s Two-Factor . Authentication, and you can now receive and approve Duo’s 2FA login verifications. ... Service Desk to request a new one. North Region: 551-993-4357 . Central ...
Guide for External Users - Ericsson Strong Authentication
access.sdt.ericsson.netSlide title 70 pt CAPITALS Slide subtitle minimum 30 pt GUIDE FOR EXTERNAL USERs – STRONG AUTHENTICATION Guide for External Users – Strong Authentication
User Guide RSA SecurID Token Requests - New York State ...
its.ny.govJan 13, 2017 · RSA SecurID is a multi-factor authentication technology that is used to protect network services. The RSA SecurID authentication mechanism consists of a “token”, either hardware or software, which is assigned to a user, and generates a dynamic authentication code at fixed intervals. That code is then used when logging into a protected
G e t A u t h e n t i ca t i o n f o r G o o g l e S e rvi ...
d35mpxyw7m7k7g.cloudfront.netThe google authentication code will do authentication and list all files in your Google Drive. Note that every time you run the following program, the code will open a web browser to ask you to input your Google account and password. To avoid inputting passwords every time, we can create a s e t t i ngs .ya m l file to save all the
Notary Request for Authentication - Oregon
sos.oregon.govand valuable documents requiring an authentication or apostille. Other forms of mail, including U.S. Postal Service "Express or Priority Mail" DO NOT . get delivered directly to our office for expedited processing and could result in a delay and/or loss of your original documents. What country are these documents being authenticated for?
HP Array Configuration Utility User Guide
h10032.www1.hp.comA web browser is used to render the user interface, but no web server is required. ACU can be run remotely from another server across a network. Authentication is handled by the operating system, ensuring that the user is an administrator on the server running ACU. Authentication is handled through the same mechanism used for Insight Manager ...
Using RADIUS Authentication for Remote Access VPN
community.checkpoint.comAppendix: Using DUO MFA as a RADIUS Server for Remote Access VPN Authentication This guide can easily be adapted to use a third-party RADIUS server (in this case DUO). DUO is typically deployed with a proxy server running on either Linux or Windows Server. In our case we will use a DUO proxy server running Windows Server 2012 R2.
Get Ready for Federated Authentication - Apple
www.apple.comFederated authentication makes it easier than ever to integrate iPad and Mac into your school’s existing environment. If your school is using Microsoft Azure Active Directory as your identity provider, you can easily set up a direct connection to Apple School Manager to provide access to Apple services for your users.
Deploying OAuth with Cisco Collaboration Solution …
www.cisco.comAuthentication is the process of confirming a person (or thing’s) identity. Traditionally this is using a username and password but could use a certificate or other proof of identity. Increasingly modern systems require multi-factor authentication …
Mutlifactor Authentication and APD iConnect Access
apd.myflorida.comAuthentication and APD iConnect Access Barbara Palmer APD Director Ron DeSantis Governor ... setting up the user account on the ID PASS system Configuring MFA Access 10 11 12. 6/2/2020 5 ... based on a person’s job, a role or multiple roles are assigned
Azure Active Directory Self-Service Password Reset ...
download.microsoft.comsecurity features like Multi-Factor Authentication and SSPR. End users will also learn how to view and manage their security methods in Azure AD. Books Source: Microsoft Press - Modern Authentication with Azure Active Directory for Web Applications (Developer Reference) 1st …
SYSADMIN1 (Reflex Secure Plus - 2 Factor Authentication ...
www.rhbgroup.comAdditional Token Request (Reflex Secure Plus - 2 Factor Authentication (2FA) via registered smartphone) Quantity Low Battery Replacement Reason Lost/Stolen Defective/Damage Low Battery Replacement Reason Lost/Stolen Defective/Damage User ID Token Serial Number Replacement Reason Lost/Stolen Defective/Damage E-mail* SYSADMIN2 SYSADMIN1 v4.7 ...
Certification, Authentication & Verification (CAV) Form
chedro3.ched.gov.phCertification, Authentication & Verification (CAV) Form CAV No. _____ REQUIREMENTS: 1. LETTER OF CONFIRMATION from the School Registrar (Original copy) 2. DIPLOMA (2 Xerox copies duly certified by the School Registrar) 3. TRANSCRIPT OF ...
Apostille or Certificate of Authentication Request Form ...
www.sos.wa.govApostille Request Form. Pg 1 | Revised 9.2019. Apostille or Certificate of Authentication Request Form (3) FEES THE FEE IS $15.00 PER DOCUMENT Number of Documents:
Selecting Secure Multi-factor Authentication Solutions
media.defense.govSep 22, 2020 · AAL native logon 2 – dependent on client, server FIPS validated (#2671) Duo Mobile Passcode SW installed on: iOS 6+ Android 3.25+ Windows Phone 2.0+ FEDRAMP14 approved Depends on compliant TLS 1.2 HTTPS (StartTLS), LDAPS Native logon uses RDP Device and User Enrollment Authenticator Revocation Authentication Agent and Proxy
SAICA GUIDANCE REMOVING AND ADDING TAXPAYER …
saicawebprstorage.blob.core.windows.netSARS will check if you if have ‘Manage Payer Rights’ on both the requesting and holding portfolio. Once verified the tax type will be transferred immediately. c) Where the owner or registered representative does not approve the ... As part of the authentication process, you will be required to enter a One-Time-Pin (OTP).
Procedure for Generating Jeevan Pramaan / Digital Life ...
www.jeevanpramaan.gov.inThe JP uses the Aadhaar platform for biometric authentication of the pensioner. For the DLC generation the pensioners needs to have Internet Connectivity, a biometric device (list of supported devices is given on the JP portal) and JP Windows/Android Client Application Software for PC/Mobile/tablet which can be downloaded
Intel WiFi Link 5100 Series
www.intel.comin both PCIe* Mini Card and Half Mini Card form factor deliver up to 300 Mbps2 of receive ... MIMO, diversity, and support for up to two antennas enable better wireless reception at the same distance when compared to 802.11a/b/g solutions ... stronger authentication and encryption mechanisms Intel® PROSet v12.04
Digital Identity Guidelines - NIST
nvlpubs.nist.govidentity services and are not intended to constrain the development or use of standards outside of this purpose. This guideline focuses on the enrollment and verification of an identity for use in digital authentication. Central to this is a process known as identity proofing in which an
Workspace ONE Boxer for iOS User Guide - VMware
docs.vmware.comSingle sign-on (SSO) is a user authentication service that allows you to use a set of login ... other enterprise applications. Workspace ONE Boxer for iOS User Guide VMware, Inc. 6. Use PIV-D Manager to Enroll into Workspace ONE Boxer. If configured by your administrator, you can use Workspace ONE PIV-D Manager to enroll into ...
PROVIDENT BENEFITS CLAIM HQP-PFF-377 CHECKLIST OF ...
www.pagibigfund.gov.phBirth Certificate of Member issued by Philippine Statistics Authority (PSA) Non-availability of Birth Record issued by PSA and Joint Affidavit of Two Disinterested Persons (notarized) 2. In all instance, wherein: a. Photocopies are submitted, the original document must be presented for authentication. b.
Welcome to Via Benefits!
documents.viabenefits.com3. When you sign in, you will get a text message on your cell phone or a call on your landline phone. The message will include a code for you to enter on the Via Benefits website for authentication. 4. Enter this code onscreen where prompted. Steps three and four will occur every 30 days to help keep your
JAN AADHAAR ENROLLMENT USING RGHS
rghs.rajasthan.gov.inThere is a aadhar based authentication consent to confirm the authenticity. If user select Agree the terms and conditions will be redirect to delete member form. Select member for delete from family, enter the reason of delete, upload document and click on ‘Sadasya Hataye ’ button.
HOW TO APPLY
www.incometaxindia.gov.inAadhaar authentication may get rejected due to wrong OTP. The problem can be resolved by entering the correct OTP. If it still gets rejected, you have to contact the UIDAI. 18. Do I need Digital Signature Certificate (DSC) for applying for PAN card through Aadhaar
Secure Acceptance Checkout API Integration Guide
developer.cybersource.comSecure Acceptance Checkout API Integration Guide | 4 Contents Configuring Payer Authentication 23 Enabling Automatic Authorization Reversals 24 Enabling Echecks 25 Enabling PayPal Express Checkout 25 Security Keys 26 Creating Security Keys 27 Merchant Notifications 28 Configuring Merchant Notifications 28 Customer Receipts 29 Configuring Customer …
Kubernetes Hardening Guide
media.defense.govMar 15, 2022 · Use strong user authentication. Create RBAC policies with unique roles for users, administrators, developers, service accounts, and infrastructure team. Audit Logging and Threat Detection Enable audit logging (disabled by default). Persist logs to ensure availability in the case of node, Pod, or container-level failure.
Certification Authentication and Verification (CAV ...
philippines.embassy.gov.auoffice of either DepEd, CHED or TESDA for the issuance of the CAV document. You will then have to bring the CAV document and academic records to the Philippine DFA to have the CAV Apostilled. The Apostille is different from the “Red Ribbon” and our requirement is a DFA Apostille. DFA Red Ribbon is not acceptable.
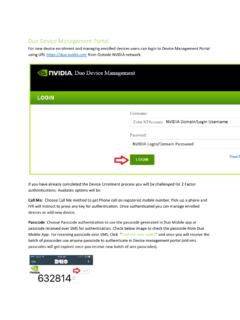
Duo Device Management Portal - Duo Self-Service Portal
duo.nvidia.comDuo? Duo Security is a two-step verification service that provides additional security for access to institutional data, servers, applications, and personal data. Duo combines modern two-factor authentication with advanced endpoint security solutions to protect users from account takeovers and data breaches during VPN connections. Why two-factor
CORPORATEPAY Corporate Portal User Manual
connectips.coma private network (Layer 2 or Layer 3), accordingly for L2/L3 access it needs to setup its network access. 4. Corporate users should have its personal email id and mobile number. 5. All the users of the CORPORATEPAY system will have to download Google Authenticator App in its mobile for two factor authentication (2FA) during login. 3.
Duo MFA Enrollment Guide - Miami
www.it.miami.eduthis option enabled Duo automatically sends an authentication request via push notification to the Duo Mobile app on your smartphone or a phone call to your device (depending on your selection). Note: It is recommended that you register at least two devices, for example, both your smartphone and your office phone.
Federal Student Aid Two Factor Authentication (TFA) How …
fsapartners.ed.govOnly physical token s issued by Federal Student Aid can be used to access Federal Student Aid systems. The TFA token must be in your physical possession when you register it, and wh en you use it to log into a Federal Student Aid system. The token generates a One -Time Password (OTP ) that is valid for 30 seconds.
RAPIDS Self Service User Guide - MilitaryCAC
militarycac.us• Activate the Personal Identity Verification (PIV) Authentication application ... Frequently Asked Questions for instructions on how to delete certificates). 2. Insert your CAC into the card reader. 3. Click Sign On at the top right corner or in the middle of the screen.
Pradhan Mantri Jan-Dhan Yojana
www.pmjdy.gov.inChallenges identified in the implementation of the Mission 40 13. Roles of major stakeholders 42 14. Launch Function 46 15. Timelines for Implementation 47. ii ... based biometric authentication from UIDAI data base. • Putting the PSBs and RRBs numbers together implies that about 5.92 crore rural households are yet to be covered. ...
Request a document Authentication or Apostille
www.govt.nzThe document must be the original document with a round seal from the Registrar of Births, Deaths and Marriages We don't authenticate or Apostille a Copy of Particulars of Marriage (that is the document you signed on your wedding day).
How to Approve or Deny a Request for FMLA Leave
www.shrm.orga Request for FMLA Leave E mployees may have a right to unpaid, job-protected leave under the federal Family ... AND AUTHENTICATION NEEDS, IF ANY On …
Configuring 802.1X Authentication Client for Windows 10
www.nyp.edu.sgWireless LAN Client Configuration Guide for Windows 10 . 1.2 In Network and Sharing Center, click on “Setup a new connection or network”. 1.3 In Setup, a connection or network, click on “Manually connect to a wireless network” and click Next.
AUTHENTICATION APPLICATION FORM - Department of …
consular.dfa.gov.phAuthentication Form as of August 2019 DFA-OCA-A-02 Revision 3 DEPARTMENT OF FOREIGN AFFAIRS Office of Consular Affairs Authentication Division AUTHENTICATION APPLICATION FORM Control No. (Do not fill this out) Pls. check box for preferred transaction Expedite After 1 working day Fee: ₱200 per document Regular After 4 working days
Similar queries
FIPS, AUTHENTICATION, Manager, User, BANKING AUTHENTICATION METHODS, Words, COVID-19 Daily Symptom Questionnaire If, Factor, Service, Request, GUIDE FOR EXTERNAL USERs, Strong Authentication, STRONG AUTHENTICATION Guide for External Users, User Guide RSA SecurID Token Requests, A u t h e n t i ca t i o n, Oregon, Authentication or apostille, HP Array Configuration Utility User Guide, System, Get Ready for Federated Authentication, Apple, Active Directory, Deploying OAuth with Cisco Collaboration Solution, Factor authentication, Based, Apostille, Selecting Secure Multi-factor Authentication Solutions, Native, Payer, Biometric authentication, Biometric, Intel, Identity, Single sign, Enterprise, Certificate, Text, Cell phone, Phone, Aadhaar, Aadhaar authentication, Secure Acceptance Checkout API, Payer Authentication, Guide, Strong, Users, Document, Authentication request, Federal Student Aid Two Factor Authentication, Federal, Register, RAPIDS Self Service User Guide, Personal Identity Verification, Instructions, Pradhan Mantri Jan-Dhan Yojana, Implementation, For Implementation, Request a document Authentication or Apostille, Approve or Deny a Request for FMLA Leave, A Request for FMLA Leave, Configuring 802.1X Authentication Client for Windows